Joseph Cox writes in: Cops Told ‘Don’t Look’ at New iPhones to Avoid Face ID Lock-Out:
…
As Apple has improved its security protections against attackers who have physical access to a phone—Touch and Face ID, the Secure Enclave Processor that handles these tools, and robust encryption used by default—law enforcement agencies have come up with varying techniques for getting into devices they seize. In the UK, police officers simulated a mugging to steal a suspect’s phone while he was using it, so it would be unlocked, and the officer repeatedly swiped the screen to make sure the phone did not close itself off again. Police lawyers determined that they would have no legal power to force the suspect to place his finger on the device, so opted for this unusual, albeit novel, approach.In the US, however, law enforcement agencies have used both technical and legal means to get into devices. Courts have compelled suspects to unlock their device with their face or fingerprint, but the same approach does not necessarily work for demanding a passcode; under the Fifth Amendment, which protects people from incriminating themselves, a passcode may be considered as “testimonial” evidence. A number of warrants have focused on forcing suspects to place their finger onto an iPhone, and, as Forbes noted in its recent report, some warrants now include boilerplate language that would cover unlocking a device with a person’s face as well. Law enforcement agencies across the country have also bought GrayKey, a small and relatively cheap device that has had success in unlocking modern iPhones by churning through different passcode combinations.
…
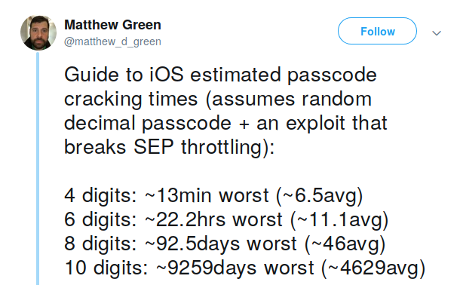
Of all the breaches of iPhone security mentioned, GreyKey is the most disturbing. It bypasses the repeated attempt limitation and GreyKey can crack a six-digit PIN in 22.2 hours (at worst) and 11.1 hours on average. Estimates in this tweet by @matthew_d_green:
While mulling over the implications of GrayKey, I found How to Set iPhone to Erase All Data After 10 Failed Passcode Attempts by Leomar Umpad.
The downside being you may be too excited (one word for it) when the door bursts open and a flash bang grenade goes off to quickly enter the wrong passcode in your iPhone. Or your freedom of movement may be restricted by armed police officers even after calm is restored.
You iPhone needs an EraseIt! app that:
- Responds to verbal commands
- User supplied command starts erasure process
- Once started, erasure process disables all input, including the power button
- Erases all data (among other things I don’t know, how effective is data erasure in iPhones?)
- (Refinement) Writes 0 or 1 to all memory locations until battery failure
Relying on passcodes reminds me of Bruce Schneier’s classification of cryptography in Applied Cryptography (2 ed.):
There are two kinds of cryptography in this world: cryptography that will stop your kid sister from reading your files, and cryptography that will stop major governments from reading your files. This book is about the latter.
Passcodes are the former.
What other requirements would you have for an EraseIt! app?
PS: Go carefully. Most government forces differ from those of Saudi Arabia (Jamal Khashoggi) only in their preference to kill with plausible deniability.