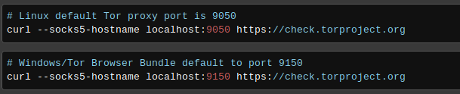
Joseph Cox details “…deanonymizing people in a targeted way using novel or unorthodox law enforcement techniques…” in The FBI Booby-Trapped a Video to Catch a Suspected Tor Sextortionist.
Not an attack on Tor per se but defeated the use of Tor none the less.
Can you spot the suspect’s error?
From the complaint:
…
F. Law Enforcement Identifies “Brian Kil’s” True IP Address
51. On June 9, 2017, the Honorable Debra McVicker Lynch authorized the execution of a Network Investigative Technique “NIT” (defined in Clause No. 1:17-mj-437) in order to ascertain the IP address associated with Brian Kil and Victim 2.
52. As set forth in the search warrant application presented to Judge Lynch, the FBI was authorized by the Court to add a small piece of code (NIT) to a normal video file produced by Victim 2, which did not contain any visual depictions of any minor engaged in sexually explicit activity. As authorized, the FBI then uploaded the video file containing the NIT to the Dropbox.com account known only to Kil and Victim 2. When Kil viewed the video containing the NIT on a computer, the NIT would disclose the true IP address associated with the computer used by Kil.
…
57. When Kil viewed the video containing the NIT on a computer the NIT disclosed the true IP address associated with the computer used by Kil.
…
Where did “Kil’s” opsec fail?
“Kil” viewed content of unknown origin on a networked computer.
“Kil” thought the content originated with Victim 2, but all remote content on the Internet should be treated as being of unknown origin.
No one knows if you are a dog on the Internet just as you don’t know if the FBI sent the video you are playing.
Content of unknown origin is examined and stays on non-networked computers. Copy text only to networked systems. If you need the original content, well, you have been warned.
You can see the full complaint at:
https://assets.documentcloud.org/documents/3914871/Hernandez-NIT-Complaint.pdf
Best practice: Remote content, even if from known source, is of unknown origin. (A comrade may have made the document, video, image, but government agents intercepted and infected it.)
PS: I’m no fan of sextortionists but I am concerned about the use of “booby-trapped” videos against political activists. (Makes you wonder about “jihadist” videos on YouTube doesn’t it?)