The First Augur Assassination Markets Have Arrived by David Floyd.
From the post:
“Killed, not die of natural causes or accidents.”
Pretty much everyone saw them coming, but it was no less disturbing when assassination markets actually began to appear on Augur, a decentralized protocol for betting on the outcomes of real-world events and that launched two weeks ago on ethereum.
The markets – which allow users to bet on the fates of prominent politicians, entrepreneurs and celebrities – in some cases explicitly specify assassination, as the quote above shows. (CoinDesk is intentionally not providing links to these markets or naming the individuals concerned.)
In addition to targeting individuals, some markets offer bets on whether mass shootings and terrorist attacks with certain minimum numbers of casualties will occur.
…
By creating a market for an assassination and placing a large “no” bet (actually, selling shares in the outcome), an individual or group could in effect place a bounty on the targeted person. The would-be assassin could then place a bet on “yes” (buy shares) and manipulate the outcome, to put it delicately.
…
An Augur assassination markets sounds like a way to democratize murder. Governments spend $billions every year killing people with their citizens exercising little or no influence of the choice of murder targets. An assassination market has the potential for a more democratic process. Or so it would seem.
The first thing you need is an Ethereum wallet. I choose a FireFox browser extension called MetaMask, but there are others, The Top 10 Best Ethereum Wallets (2018 Edition) by Sudhir Khatwani.
Next up, the Augur app. (GitHub) Augur isn’t long on documentation for the beginning users so here are screen shots and text about my installation process.
- I used
sudo dpkg -i linux-Augur-1.0.7.deb, encountered dependency issues and so then ranapt-get install -f.OK, first screen shot, the default screen when I started Augur from the panel bar:
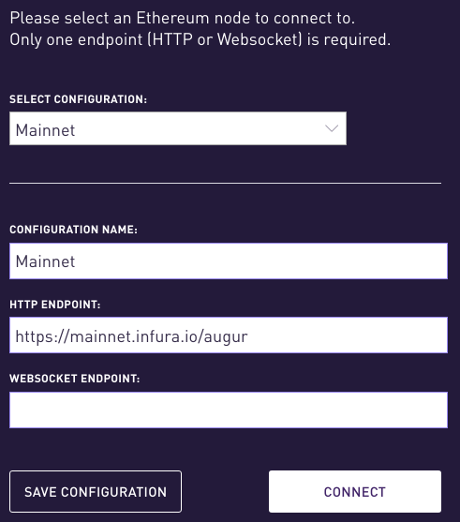
I accepted all of the defaults, saved the configuration.
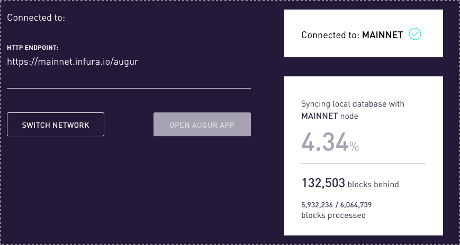
- After selecting connect, with the default configuration values, this is the next screen:
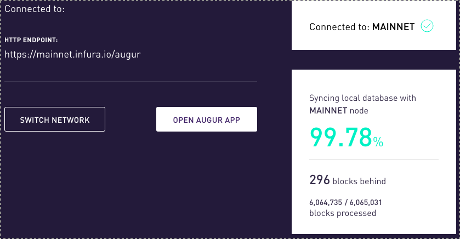
As you can tell by the % meter, this is going to take a while. I didn’t time it precisely but would guess it is 90 minutes or longer to synch up.
- You probably don’t have to wait as long as I did but when it was over 99% synched, I connected with the Augur app:
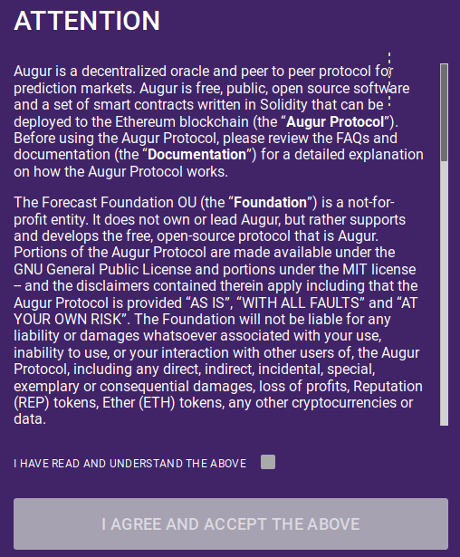
- I should have expected it, next was the scroll down agreement to activate the checkbox and then agree to terms window, which in part reads:
Right! I’ve taken numerous steps to conceal both my identity and activity, so sure, I’m going to try to tag Augus in court if something goes sideways.
Sigh, old habits die hard.
- The Augur default homepage (in part only):
Then you choose “MARKETS” in the upper left-hand corner and look for assasinations.
A lot of installing to realize the reason why:
(CoinDesk is intentionally not providing links to these markets or naming the individuals concerned.)
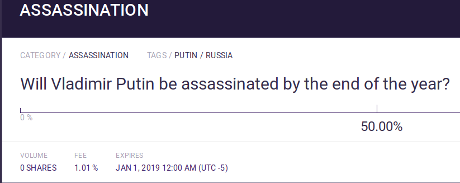
There’s only one (1) such market and it has only one target, without any “no” money. As you might suspect, it’s the fav of all late night talk show hosts:
I don’t regret installing the new tools but was disappointed by the “assassination market clickbait” approach.
PS: Putin doesn’t even make my top 100. You?