Approach the webpage: Crowdfense Vulnerability Research Hub with caution! By posting:
Crowdfense budget for its first public Bug Bounty Program, launched April 2018, is $10 million USD.
Payouts for full-chain, previously unreported, exclusive capabilities range from $500,000 USD to $3 million USD per successful submission. Partial chains will be evaluated on a case-by-case basis and priced proportionally.
Within this program, Crowdfense evaluates only fully functional, top-quality 0-day exploits affecting the following platforms and products:
…
I have violated website restrictions, https://www.crowdfense.com/terms.html, clauses 1 and 4:
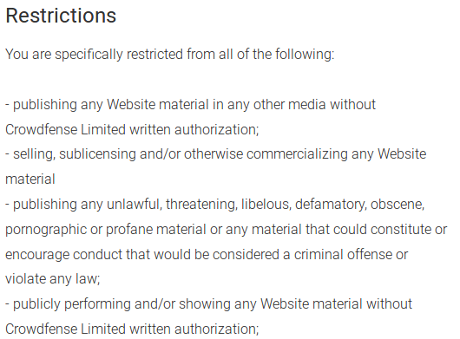
Subjecting me to:
…
Governing Law & Jurisdiction
These Terms will be governed by and interpreted in accordance with the laws of the United Arab Emirates, and you submit to the non-exclusive jurisdiction of the State and Federal Courts located in the Emirate of Abu Dhabi for the resolution of any disputes.
…
Sound absurd? It certainly is but no more absurd than the EU attempting to be the tail that wags the dog on issues of being forgotten or privacy.
The United Arab Emirates has as deep and storied a legal tradition as the EU but neither should be applied to actors outside their geographic borders.
If I am hosting content in the EU or United Arab Emirates, I am rightly subject to their laws. On other hand, if I am hosting content or consuming content outside their geographic boundaries, it’s absurd to apply their laws to me.
If the EU or United Arab Emirates wish to regulate (read censor) Internet traffic within their borders, it’s wrong-headed but their choice. But they should not be allowed to make decisions about Internet traffic for other countries.

