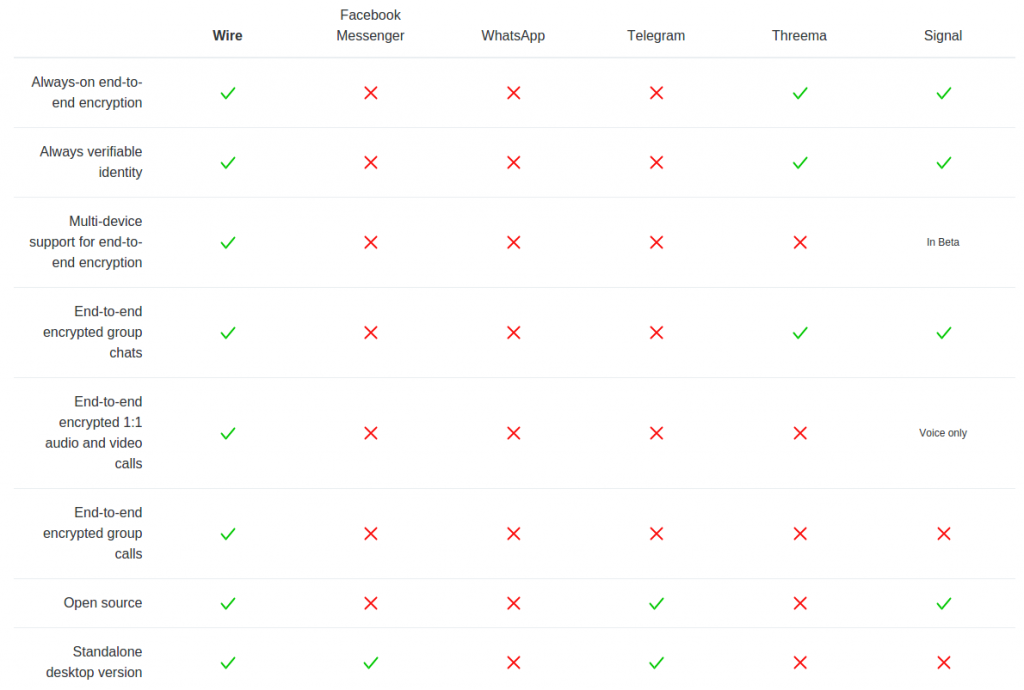
Passwords: Philology, Security, Authentication by Brian Lennon.
Disclaimer: I haven’t seen Passwords, yet, but it’s description and reviews prompted me to mention it here.
That and finding an essay with the same titie, verbatim, by the same author, published in Diacritics, Volume 43.1 (2015) 82-104. Try: Passwords: Philology, Security, Authentication. (Hosted on the Academia site so you will need an account (free) to download the essay (also free).
From the publisher:
Cryptology, the mathematical and technical science of ciphers and codes, and philology, the humanistic study of natural or human languages, are typically understood as separate domains of activity. But Brian Lennon contends that these two domains, both concerned with authentication of text, should be viewed as contiguous. He argues that computing’s humanistic applications are as historically important as its mathematical and technical ones. What is more, these humanistic uses, no less than cryptological ones, are marked and constrained by the priorities of security and military institutions devoted to fighting wars and decoding intelligence.
Lennon’s history encompasses the first documented techniques for the statistical analysis of text, early experiments in mechanized literary analysis, electromechanical and electronic code-breaking and machine translation, early literary data processing, the computational philology of late twentieth-century humanities computing, and early twenty-first-century digital humanities. Throughout, Passwords makes clear the continuity between cryptology and philology, showing how the same practices flourish in literary study and in conditions of war.
Lennon emphasizes the convergence of cryptology and philology in the modern digital password. Like philologists, hackers use computational methods to break open the secrets coded in text. One of their preferred tools is the dictionary, that preeminent product of the philologist’s scholarly labor, which supplies the raw material for computational processing of natural language. Thus does the historic overlap of cryptology and philology persist in an artifact of computing—passwords—that many of us use every day.
Reviews (from the website):
“Passwords is a fascinating book. What is especially impressive is the author’s deft and knowing engagements with both the long histories of computational text processing and the many discourses that make up literary philology. This is just the sort of work that the present mania for the digital demands, and yet books that actually live up to those demands are few and far between. Lennon is one of the few scholars who is even capable of managing that feat, and he does so here with style and erudition.”—David Golumbia, Virginia Commonwealth University
“A stunning intervention, Passwords rivets our attention to the long history of our present fascination with the digital humanities. Through a series of close, contextual readings, from ninth-century Arabic philology and medieval European debates on language to twentieth-century stylometry and machine translation, this book recalls us to a series of engagements with language about which ‘all of us—we scholars, we philologists,’ as Lennon puts it, ought to know more. Passwords is eloquent and timely, and it offers a form of deep, institutional-lexical study, which schools us in a refusal to subordinate scholarship in the humanities to the identitarian and stabilizing imperatives of the national-security state.”—Jeffrey Sacks, University of California, Riverside
Not surprisingly, I think a great deal was lost when humanities, especially those areas focused on language, stopped interacting with computer sciences. Sometime after the development of the first compilers but I don’t know that history in detail. Suggested reading?