Weapon Systems Cybersecurity: DOD Just Beginning to Grapple with Scale of Vulnerabilities
From the webpage:
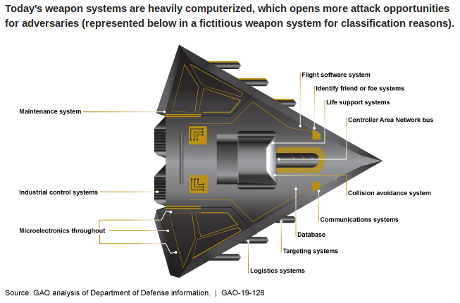
The cited reason for the “fictitious weapon system” is “classification reasons.”
Maybe, but identifying weaknesses in named weapon systems, encourages use of those security flaws as excuses for flaws in other systems. “Everybody has flaw ….. You can’t penalize me for a market standard flaw.”
Under the section title: Test Teams Easily Took Control (page 22):
…
Test teams were able to defeat weapon systems cybersecurity controls meant to keep adversaries from gaining unauthorized access to the systems. In one case, it took a two-person test team just one hour to gain initial access to a weapon system and one day to gain full control of the system they were testing. Some programs fared better than others. For example, one assessment found that the weapon system satisfactorily prevented unauthorized access by remote users, but not insiders and near-siders. Once they gained initial access, test teams were often able to move throughout a system, escalating their privileges until they had taken full or partial control of a system. In one case, the test team took control of the operators’ terminals. They could see, in real-time, what the operators were seeing on their screens and could manipulate the system. They were able to disrupt the system and observe how the operators responded. Another test team reported that they caused a pop-up message to appear on users’ terminals instructing them to insert two quarters to continue operating. Multiple test teams reported that they were able to copy, change, or delete system data including one team that downloaded 100 gigabytes, approximately 142 compact discs, of data.
…
For “security” reasons none of the systems were named, guranteeing the same failing vendors in the same congressional districts will continue to produce failing weapon systems.
Not only does opportunity knock for present US weapon systems, but additional opportunities await in every country where such systems are sold.
Remember, “…one hour to gain initial access … one day to gain full control….” If that’s not opportunity, I don’t know what is.