Data Breach Digest (Verizon)
From the report:
The Situation Room
Data breaches are complex affairs often involving some combination of human factors, hardware devices, exploited configurations or malicious software. As can be expected, data breach response activities—investigation, containment, eradication, notification, and recovery—are proportionately complex.
These response activities, and the lingering post-breach aftereffects, aren’t just an IT security problem; they’re an enterprise problem involving Legal Counsel, Human Resources, Corporate Communications and other Incident Response (IR) stakeholders. Each of these stakeholders brings a slightly different perspective to the breach response effort.
Last year, thousands of IR and cybersecurity professionals delved into the inaugural “Data Breach Digest—Scenarios from the Field” (aka “the RISK Team
Ride-Along Edition”) to get a first-hand look into the inner workings of data breaches from an investigative response point of view (PoV).Continued research into our recent caseload still supports our initial inklings that just over a dozen or so prevalent scenarios occur at any given time. Carrying forward from last year, we have come to realize that these data breach scenarios aren’t so much about threat actors, or even about the vulnerabilities they exploited, but are more about the situations in which the victim organizations and their IR stakeholders find themselves. This gives each scenario a distinct personality … a unique persona, per se.
This year, for the “Data Breach Digest—Perspective is Reality” (aka “the IR Stakeholder Edition”), we took a slightly different approach in bringing these scenarios to life. Each scenario narrative—again, based on real-world data breach response activities—is told from a different stakeholder PoV. As such, the PoV covers their critical decision pivot points, split-second actions taken, and crucial lessons learned from cases investigated by us – the Verizon RISK Team.
… (emphasis in original)
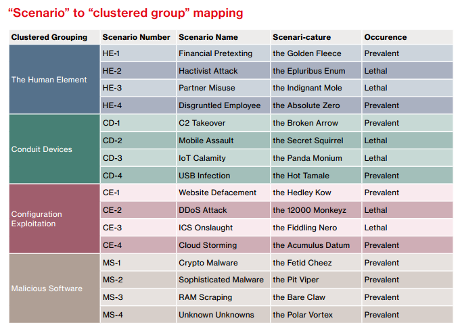
The “scenario” table mapping caught my eye:
The Scenari-cature names signal an amusing and engaging report awaits!
A must read!
To make up for missing this last year, here’s a link to 2016 Data Breach Digest.