In Lowering the Bar for Leakers I proposed this method for leaking login credentials:
- Write login credentials (not your own), login URL, on paper
- Mail to (news address) – no return address
- News Media: Destroys all leaked credentials upon receipt
Easier than the convolutions you will find at: How easy is it to securely leak information to some of America’s top news organizations? This easy or Attention Federal Employees: If You See Something, Leak Something, but we can do better.
A Universal (nearly) and Secure Leaking Point
Can you think of one characteristic shared by almost all websites? Aside from being on the Web?
The ability to create an account for news and updates!
Like this page from the New York Times:
Warning: Leak login credentials to sites using the https protocol only.
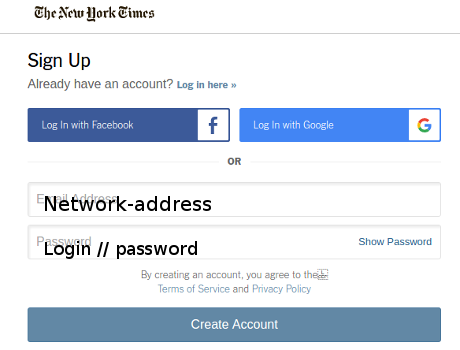
Leaking access to a publicly accessible server
Leaking your sysadmin’s, boss’s, co-worker’s credentials, you enter:
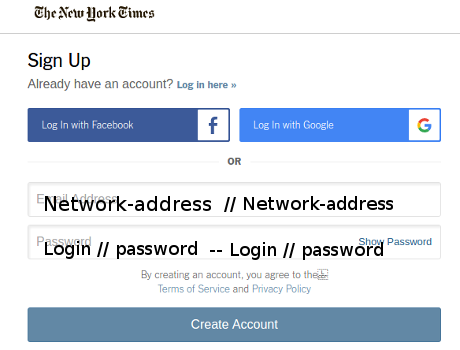
Leaking access to a server on a restricted network
For servers or resources requiring more than one set of credentials, say on a secure network, again using your sysadmin’s, boss’s, co-worker’s credentials, you enter:
Leaking In Two Steps
The leaking of login credentials (not your own) is two steps:
- Create account from non-work computer
- Enter login credentials as account details
You are protected by:
- SSL encryption
- Safety in numbers – Study finds that 97% of large companies have had credentials leaked online
- Credential duplication is a well-known fact – 17% of passwords are “123456”
- Not facing the risks of a sneakernet thief to steal, transport and deliver data in hard copy or digital format
This technique will work with agencies, banks, corporations, courts, governments, legislatures, PACs, anywhere that requires digital login credentials.
I used email and password fields here but that is just an artifact of the New York Times form. Other parts of a form and other separators are certainly possible.
PS: Don’t leak credentials to me because my site doesn’t have SSL (right now) and I’m not in full control of the server.
Personally, if I were to accept leaked credentials, I would store that data on a RAM disk.