Intelligence Gathering & Its Relationship to the Penetration Testing Process by Dimitar Kostadinov.
From the post:
Penetration testing simulates real cyber-attacks, either directly or indirectly, to circumvent security systems and gain access to a company’s information assets. The whole process, however, is more than just playing automated tools and then proceed to write down a report, submit it and collect the check.
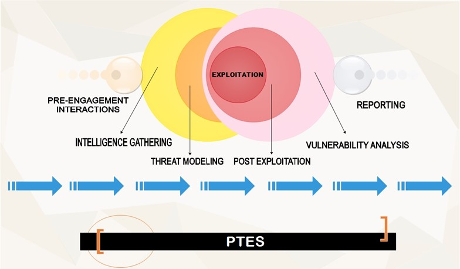
The Penetration Testing Execution Standard (PTES) is a norm adopted by leading members of the security community as a way to establish a set of fundamental principles of conducting a penetration test. Seven phases lay the foundations of this standard: Pre-engagement Interactions, Information Gathering, Threat Modeling, Exploitation, Post Exploitation, Vulnerability Analysis, Reporting.
Intelligence gathering is the first stage in which direct actions against the target are taken. One of the most important ability a pen tester should possess is to know how to learn as much as possible about a targeted organization without the test has even begun – for instance, how this organization operates and its day-to-day business dealings – but most of all, he should make any reasonable endeavor to learn more about its security posture and, self-explanatory, how this organization can be attacked effectively. So, every piece of information that a pen tester can gather will provide invaluable insights into essential characteristics of the security systems in place.
…
Great introduction to intelligence gathering with links to some of the more obvious tools and coverage of common techniques.
As your tradecraft improves, so will your list of tools and techniques.
My only reservation is that Dimitar doesn’t mention how you capture the intelligence you have gathered.
Text document edited in Emacs?
Word document (shudder) under control of a SharePoint (shudder, shudder) server?
Spreadsheet?
Graph/Topic Map?
Intelligence gathering results in non-linear discovery arbitrary relationships and facts. Don’t limit yourself to a linear capture methodology, however necessary linear reports are for others.
My vote is with graphs/topic maps.
Since he didn’t mention recording your intelligence, Dimitar also doesn’t discuss how you secure your captured intelligence. But that’s a topic for another post.