Anti-virus products, security devices affected by 7-Zip flaws by David Bisson.
From the post:
…
But users be warned. Cisco Talos recently discovered multiple vulnerabilities in 7-Zip that are more serious than regular security flaws. As explained in a blog post by Marcin Noga and Jaeson Schultz, two members of the Cisco Talos Security Intelligence & Research Group:“These type of vulnerabilities are especially concerning since vendors may not be aware they are using the affected libraries. This can be of particular concern, for example, when it comes to security devices or antivirus products. 7-Zip is supported on all major platforms, and is one of the most popular archive utilities in-use today. Users may be surprised to discover just how many products and appliances are affected.”
Cisco Talos has identified two flaws in particular. The first (CVE-2016-2335) is an out-of-bounds read vulnerability that exists in the way 7-Zip handles Universal Disk Format (UDF) files. An attacker could potentially exploit this vulnerability to achieve arbitrary code execution.
…
The “many products and appliances” link results in:
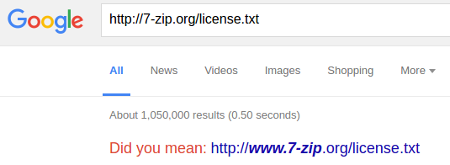
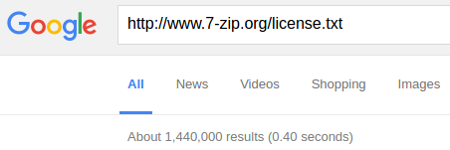
If you use the suggested search string:
Every instance of software running a vulnerable 7-Zip library is subject to this hack. A number likely larger than the total 2,490,000 shown by these two searches.
For open source software, you can check to see if it has been upgraded to 7-Zip, version 16.0.
If you have non-open source software, how are you going to check for the upgrade?
Given the lack of liability under the usual EULA, are you really going to take a vendor’s word for the upgrade?
The vulnerable 7-Zip library is a great poster child for open source software.
Not only for the discovery of flaws but to verify vendors have properly patched those flaws.