[STD = Security Transmitted Disease]
Internet-connected Hello Barbie doll gets bitten by nasty POODLE crypto bug by Dan Goodin.
From the post:
A recent review of the Internet-connected Hello Barbie doll from toymaker Mattel uncovered several red flags. Not only did the toy use a weak authentication mechanism that made it possible for attackers to monitor communications the doll sent to servers, but those servers were also vulnerable to POODLE, an attack disclosed 14 months ago that breaks HTTPS encryption.
The vulnerabilities, laid out in a report published Friday by security firm Bluebox Labs, are the latest black eye for so-called “Internet of Things” devices. The term is applied to appliances and other everyday devices that are connected to the Internet, supposedly to give them a wider range of capabilities. The Hello Barbie doll is able to hold real-time conversations by uploading the words a child says to a server. Instant processing on the server then allows the doll to provide an appropriate response.
Bluebox researchers uncovered a variety of weaknesses in the iOS and Android app developed by Mattel partner ToyTalk. The apps are used to connect the doll to a nearby Wi-Fi networks. The researchers also reported vulnerabilities in the remote server used to communicate with the doll.
…
Insecure baby monitors, hacked dolls are only the leading edges of the Insecure Internet of Things (IIoT).
Dan’s post has the details of the Security-Transmitted-Disease (STD) that can infect Hello Barbie servers and hence the dolls themselves.
When dolls, toys and other devices develop video capabilities, amateur porn will explode on the Insecure Internet of Things (IIoT). With or without the consent of the porn participants.
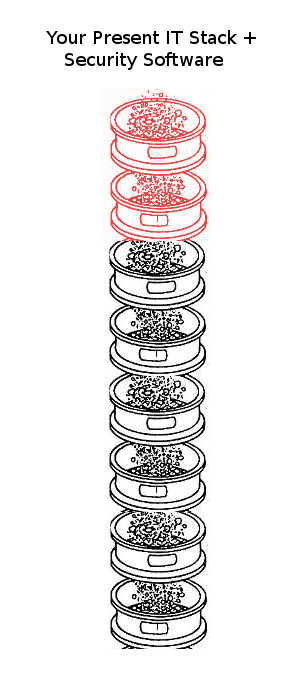
If you want a secure internet-of-things, the avoid the sieve stacking stacking strategy of current software fixes, which layers broken security software on top of broken software:
Software security starts from the bottom of your software stack and goes upward.
For all the wailing of software developers about the inability to have perfect software, realize that sql injection attacks were the #1 attack in 2013. That is more than fifteen years after the attack was documented.
Don’t buy into the “we can build perfect software” scam. No one is expecting perfect software, just software that doesn’t have 5+ year old flaws in it.
Is that too much to expect?
Heavy civil penalties for 5+ year old bugs in software might help the software industry remember to avoid such bugs.
[…] Does Your Hello Barbie Have An STD? (IIoT) Patrick Durusau […]
Pingback by Links 12/7/15, Pearl Harbor Day | naked capitalism — December 7, 2015 @ 6:57 am