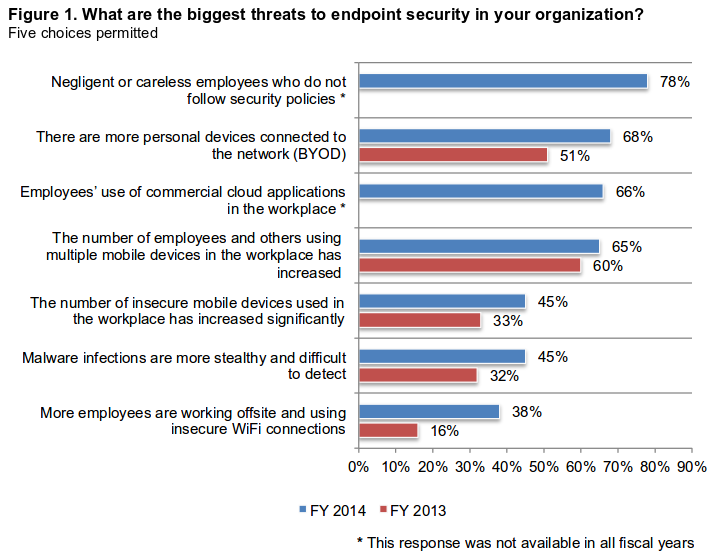
From: 2015 State of the Endpoint Report: User-Centric Risk
Negligent or careless employees are the #1 threat. OK, but except for malware, the rest of the choices focus on network technologies, all of which are insecure to varying degrees.
What two (2) threats are almost as big as #1 but aren’t listed here?
What about email and web browsers? Aren’t those typical vectors used to gain entry to endpoints?
Avoiding Phishing, Enterprise Wide
Imagine if your email server was configured to reject all email that does not originate from (yourcompany).com. How many phishing emails do you think management down to the least person with an email account would get in their daily email? Moreover, I assume you have control over email clients and no email can reach an employees computer without passing through your email server. Yes?
By taking control of incoming email, you can greatly reduce the risk of phishing emails and other insecurities being introduced into your network. No communication from off-site is ever 100% safe but reducing the amount of communication reduces your risk.
Avoiding Malicious Websites, Enterprise Wide
A large number of enterprises rely upon firewalls on a daily basis but given the prevalence of malicious websites, either firewalls are not used widely enough or not configured properly.
Reducing your risk from web browsers could be an exercise in big data for your IT staff. Start tracking the web traffic from all browsers in your enterprise and over a period of months you can build up a white-list of URLs for particular department. Assuming that you purge the white-list of sites irrelevant to that department’s function, as approved by its manager, implement that as a white-list in your firewall. (I assume you are going to check to make sure the sites on the white-list are not themselves malicious.)
That avoids you guessing what is useful for particular departments and enables you to avoid all manner of hazards, such as music download sites, etc.
It would take more effort than securing email but would greatly reduce yet another attack vector.
If anyone protests that they need unfettered access to the Internet, supply them with a standalone machine that is outside of the firewall with its drives, USB ports, etc. all glued shut. To avoid attempts at data transfer from outside of your firewall to inside your firewall. (I would assume that gluing all such access points shut was routine but the Snowden and Manning proved otherwise.)
Summary
If you float either of these proposals in your enterprise, be prepared for push-back. Users think they have some vested interest in making poor decisions with regard to your network security. Management encourages that by not focusing on the people problem that lies at the root of most security breaches, preferring instead to dream of pie-in-the-sky technology answers.
Perhaps shareholders should become aware of such recommendations when management is attempting to explain away its latest major data breach, post your making the recommendations.
PS: Users who insist on being security risks should be enabled to become security risks, for some other enterprise. Cybersecurity, liability is coming.