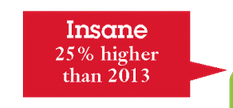
Did you know that record leakage in 2014 was “insane?” (2015 following the same security threat trend as 2014 by Neil Ford.)
IBM X-Force Threat Intelligence Quarterly reports that the number of records leaked in 2014 were 25% higher than 2013, or as shown on their graphic:
Leaking 1 billion records in 2014 is a high water mark in terms of records but it isn’t “insane.”
Even cloud bursts, breaches of cloud infrastructure that increase the percentage of leaked records over the prior year by 1% or more, can’t fairly be called “insane.”
If you want to use “insane” with cybersecurity, here is the current status of incentives for security:
Financial incentives for security — None. See: The reason companies don’t fix cybersecurity [Same reason software is insecure].
Financial incentives for hacking — Numerous, ranging from credit card fraud, identity theft, corporate espionage, etc.
That is an “insane” situation.
What is being done about it?
Congress is considering: The Protecting Cyber Networks Act, which is summarized in part as:
2014 will be known as the year of the cyber breach. High profile attacks are a main topic of conversation in the boardroom and at the dinner table. Every day, nation-state actors and criminals target America’s businesses for cyber espionage and theft. These hackers steal our intellectual property, trade secrets and even sensitive government information. The same actors who conduct cyber espionage are also capable of significant offensive cyber attacks that could degrade or damage vital private-sector infrastructure.
The Protecting Cyber Networks Act enables private companies to share cyber threat indicators with each other and, on a purely voluntary basis, with the federal government but not through the NSA or the Department of Defense, all while providing strong protections for privacy and civil liberties. At the same time, the bill makes clear that defense contractors can continue to share cyber threat information with the Department of Defense when required to do so by another law, regulation, or contract.
Voluntary information sharing with the federal government helps improve the government’s ability to protect America against foreign cyber threats. It also gives our intelligence agencies tips and leads to help them find advanced foreign cyber hackers
overseas. That intelligence allows the government to provide, in turn, even better cyber threat indicators back to the private sector to help companies protect themselves.
…
Are you familiar with the term farce?
First, the summary claims information is not shared with the NSA or DoD (second paragraph), but then in the third paragraph, “…gives our intelligence agencies….” Either they are using “intelligence agencies” in a highly usual way or they have forgotten what they just wrote.
Second, “voluntary sharing” of cyber threat indicators does not address the imbalance of incentives for computer security.
The Protecting Cyber Networks Act is an “insane” response to current issues in computer security.
Want one step towards a “sane” solution for computer security? Take the Sony breach for example. The top 10% of their employees in terms of compensation forfeit 20% of their current retirement and stock benefits.
If Sony executives had “skin in the game,” security at Sony would be far more robust than it was last year.