The Motherboard Guide to Avoiding State Surveillance by Sarah Jeong.
From the post:
In the wake of September 11th, the United States built out a massive surveillance apparatus, undermined constitutional protections, and limited possible recourse to the legal system.
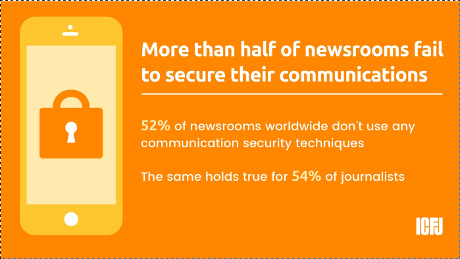
Given the extraordinary capabilities of state surveillance in the US—as well as the capabilities of governments around the world—you might be feeling a little paranoid! It’s not just the NSA—the FBI and even local cops have more tools at their disposal to snoop on people than ever before. And there is a terrifying breadth of passive and unexpected surveillance to worry about: Your social media accounts can be subpoenaed, your emails or calls can be scooped up in bulk collection efforts, and your cell phone metadata can be captured by Stingrays and IMSI catchers meant to target someone else.
Remember, anti-surveillance is not the cure, it’s just one thing you can do to protect yourself and others. You probably aren’t the most at-risk person, but that doesn’t mean you shouldn’t practice better security. Surveillance is a complicated thing: You can practice the best security in the world, but if you’re sending messages to someone who doesn’t, you can still be spied on through their device or through their communications with other people (if they discuss the information you told them, for instance).
That’s why it’s important that we normalize good security practices: If you don’t have that much to be afraid of, it’s all the more important for you to pick up some of these tools, because doing that will normalize the actions of your friends who are, say, undocumented immigrants, or engaged in activism. Trump’s CIA Director thinks that using encryption “may itself be a red flag.” If you have “nothing to hide,” your use of encryption can actually help people at risk by obfuscating that red flag. By following this guide, you are making someone else safer. Think of it as herd immunity. The more people practice good security, the safer everyone else is.
The security tips provided earlier in this guide still apply: If you can protect yourself from getting hacked, you will have a better shot at preventing yourself from being surveilled (when it comes to surveilling iPhones, for instance governments often have few options besides hacking the devices). But tech tools don’t solve all problems. Governments have a weapon in their hands that criminal hackers do not: the power of the law. Many of the tips in this section of the guide will help you not only against legal requests and government hacking, but also against anyone else who may be trying to spy on you.
You don’t have to turn yourself into a security expert. Just start thinking about your risks, and don’t be intimidated by the technology. Security is an ongoing process of learning. Both the threats and the tools developed to address them are constantly changing, which is one of the reasons why privacy and security advice can often seem fickle and contradictory. But the tips below are a good starting point.
…
Jeong writes a great post but like most of you, what I need is a security cheat sheet so I start off everyday with the same standard security practices.
Read Jeong’s post but think about creating a personalized security cheat sheet that requires your initials at the start of each day and note any security fails on your part for that day.
At the end of each week, review your security fails for patterns and/or improvements.
What’s on your security cheat sheet?