From the post:
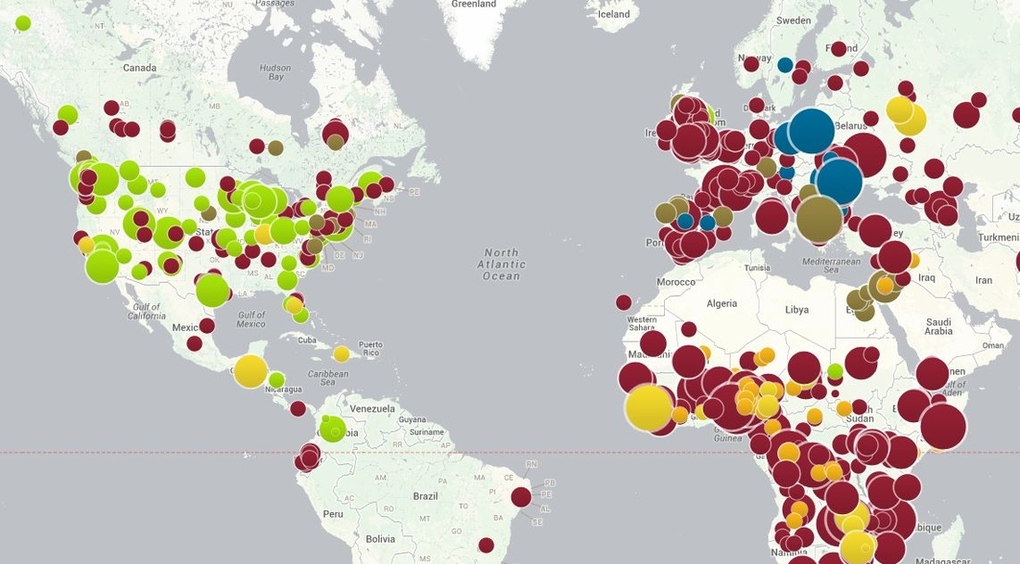
Today, we’d also like to announce the availability of a completely new and updated version of the Norse Live Attack Map. When we posted our first map back in late 2012, we did not really think much about it to be honest. Norse CTO Tommy Stiansen created it on a whim one weekend using mostly open source code, and attack maps are not necessarily a new concept. Like a lot of things, it was created out of a need for a quick and easy way for people to visualize the global and live nature of Norse’s threat intelligence platform. While the activity on the map is just a small subset (less than 1%) of the total attack traffic flowing into the Norse platform at any point in time, map visualizations can be a powerful way to communicate time-based geographic data sets.
Over the past year, the reaction by all types of people to the map has been great and we’ve received a lot of requests for enhancements and new features. Like all early stage companies, we’ve had to focus our development efforts and resources. That meant that improvements to the map were often put on the back burner. Having a new and improved map in the Norse booth at RSA 2014 provided a great incentive and target date for the team however, and we showed a preview version at the show. Aside from the completely new visual design, here is a summary of the new features.
Interesting eye candy for a Monday morning!
While the IP origins of attacks are reported, the IP targets of attacks are not.
Possible artifact of when I loaded the attack map but the United States had low numbers for being on the attack. At least until shortly after 10 A.M. East Coast time. Do you think that has anything to do with the start of the workday on the East Coast? 😉
BTW, from under the “i” icon on the Norse map:
Norse exposes its threat intelligence via high-performance, machine-readable APIs in a variety of forms. Norse also provides products and solutions that assist organizations in protecting and mitigating cyber attacks.
That must be where the target IPs are located. Maybe they offer a “last month’s data” discount of some sort. Will inquire.
Just a random observation but South American, Africa and Australia are mostly or completely dark. No attacks, no attackers. Artifact of the collection process?
Mapping IPs, route locations, attack vectors, with physical and social infrastructures could be quite interesting.
PS: If you leave the webpage open in a tab and navigate to another page, cached updates are loaded, resulting in a wicked display.