That was quick! Version 9.0.1 of GHIDRA is available for downloading. Release notes.
March 27, 2019
December 3, 2018
Distributed Denial of Secrets (#DDoSecrets) – There’s a New Censor in Town
Distributed Denial of Secrets (#DDoSecrets) (ddosecretspzwfy7.onion/)
From a tweet by @NatSecGeek:
Distributed Denial of Secrets (#DDoSecrets), a collective/distribution system for leaked and hacked data, launches today with over 1 TB of data from our back catalogue (more TK).
Great right? Well, maybe not so great:
Our goal is to preserve info and ensure its available to those who need it. When possible, we will distribute complete datasets to everyone. In some instances, we will offer limited distribution due to PII or other sensitive info. #DDoSecrets currently has ~15 LIMDIS releases.
…
As we’re able, #DDoSecrets will produce sanitized versions of these datasets for public distribution. People who can demonstrate good cause for a copy of the complete dataset will be provided with it.
Rahael Satter in Leak site’s launch shows dilemma of radical transparency documents the sad act of self-mutilation (self-censorship) by #DDoSecrets.
Hosting the Ashley Madison hack drew criticism from Joseph Cox (think Motherboard) and Gabriella Coleman (McGill University anthropologist). The Ashley Madison data is available for searching (by email for example https://ashley.cynic.al/), so the harm of a bulk release isn’t clear.
What is clear is the reasoning of Coleman:
…
Best said the data would now be made available to researchers privately on a case-by-case basis, a decision that mollified some critics.“Much better,” said Coleman after reviewing the newly pared-back site. “Exactly the model we might want.”
…
I am not surprised this is the model Coleman wants, academics are legendary for treating access as a privilege, thus empowering themselves to sit in judgment on others.
Let me explicitly say that I have no doubts that Emma Best will be as fair handed with such judgments as anyone.
But once we concede any basis for censorship, the withholding of information of any type, then we are cast into a darkness from which there is no escape. A censor claims to have withheld only X, but how are we to judge? We have no access to the original data. Only its mutilated, bastard child.
Emma Best is likely the least intrusive censor you can find but what is your response when the CIA or the NSA makes the same claim?
Censorship is a danger when practiced by anyone for any reason.
Support and leak to the project but always condition deposits on raw leaking by #DDoSecrets.
February 1, 2018
NSA Exploits – Mining Malware – Ethics Question
New Monero mining malware infected 500K PCs by using 2 NSA exploits
From the post:
It looks like the craze of cryptocurrency mining is taking over the world by storm as every new day there is a new malware targeting unsuspecting users to use their computing power to mine cryptocurrency. Recently, the IT security researchers at Proofpoint have discovered a Monero mining malware that uses leaked NSA (National Security Agency) EternalBlue exploit to spread itself.
…
The post also mentions use of the NSA exploit, EsteemAudit.
A fair number of leads and worth your time to read in detail.
I suspect most of the data science ethics crowd will down vote the use of NSA exploits (EternalBlue, EsteemAudit) for cyrptocurrency mining.
Here’s a somewhat harder data science ethics question:
Is it ethical to infect 500,000+ Windows computers belonging to a government for the purpose of obtaining internal documents?
Does your answer depend upon which government and what documents?
Governments don’t take your rights into consideration. Should you take their laws into consideration?
October 5, 2017
Software McCarthyism – Wall Street Journal and Kaspersky Lab
The Verge reports this instance of software McCarthyism by the Wall Street Journal against Kaspersky Lab saying:
…
According to the report, the hackers seem to have identified the files — which contained “details of how the U.S. penetrates foreign computer networks and defends against cyberattacks” — after an antivirus scan by Kaspersky antivirus software, which somehow alerted hackers to the sensitive files.
… (emphasis added)
Doesn’t “…somehow alerted hackers to the sensitive files…” sound a bit weak? Even allowing for restating the content of the original WSJ report?
The Wall Street Journal reports in Russian Hackers Stole NSA Data on U.S. Cyber Defense:
Hackers working for the Russian government stole details of how the U.S. penetrates foreign computer networks and defends against cyberattacks after a National Security Agency contractor removed the highly classified material and put it on his home computer, according to multiple people with knowledge of the matter.
The hackers appear to have targeted the contractor after identifying the files through the contractor’s use of a popular antivirus software made by Russia-based Kaspersky Lab, these people said.
…
U.S. investigators believe the contractor’s use of the software alerted Russian hackers to the presence of files that may have been taken from the NSA, according to people with knowledge of the investigation. Experts said the software, in searching for malicious code, may have found samples of it in the data the contractor removed from the NSA.
But how the antivirus system made that determination is unclear, such as whether Kaspersky technicians programed the software to look for specific parameters that indicated NSA material. Also unclear is whether Kaspersky employees alerted the Russian government to the finding.
Investigators did determine that, armed with the knowledge that Kaspersky’s software provided of what files were suspected on the contractor’s computer, hackers working for Russia homed in on the machine and obtained a large amount of information, according to the people familiar with the matter.
…
The facts reported by the Wall Street Journal support guilt by association style McCarthyism but in a software context.
Here are the only facts I can glean from the WSJ report and common knowledge of virus software:
- NSA contractor removed files from NSA and put them on his home computer
- Home computer was either a PC or Mac (only desktops supported by Kaspersky)
- Kaspersky anti-virus software was on the PC or Mac
- Kaspersky anti-virus software is either active or runs at specified times
- Kaspersky anti-virus software scanned the home computer one or more times
- Hackers stole NSA files from the home computer
That’s it, those are all the facts reported in the Wall Street Journal “story,” better labeled a slander against Kaspersky Lab.
The following claims are made with no evidence whatsoever:
- “after identifying the files through the contractor’s use of a popular antivirus software made by Russia-based Kaspersky Lab”
- “believe the contractor’s use of the software alerted Russian hackers to the presence of files”
- “whether Kaspersky technicians programed the software to look for specific parameters”
- “unclear is whether Kaspersky employees alerted the Russian government to the finding”
- “armed with the knowledge that Kaspersky’s software provided”
The only evidence in the possession of investigators is the co-locations of the NSA files and Kaspersky anti-virus software on the same computer.
All the other beliefs, suppositions, assumptions, etc., of investigators are attempts to further the government’s current witch hunt against Kaspersky Labs.
The contractor’s computer likely also had MS Office, the home of more than a few security weaknesses. To say nothing of phishing emails, web browsers, and the many other avenues for penetration.
As far as “discovering” the contractor to get the files in question, it could have been by chance and/or the contractor bragging to a waitress about his work. We’re not talking about the sharpest knife in the drawer on security matters.
Judging hacking claims based on co-location of software is guilt by association pure and simple. The Wall Street Journal should not dignify such government rumors by reporting them.
September 14, 2017
Self-Censorship and Privilege on the Internet
Sloppy U.S. Spies Misused A Covert Network For Personal Shopping — And Other Stories From Internal NSA Documents by Micah Lee, Margot Williams, Talya Cooper.
From the post:
NSA agents successfully targeted “the entire business chain” connecting foreign cafes to the internet, bragged about an “all-out effort” to spy on liberated Iraq, and began systematically trying to break into virtual private networks, according to a set of internal agency news reports dating to the first half of 2005.
British spies, meanwhile, were made to begin providing new details about their informants via a system of “Intelligence Source Descriptors” created in response to intelligence failures in Iraq. Hungary and the Czech Republic pulled closer to the National Security Agency.
And future Intercept backer Pierre Omidyar visited NSA headquarters for an internal conference panel on “human networking” and open-source intelligence.
These stories and more are contained in a batch of 294 articles from SIDtoday, the internal news website of the NSA’s core Signals Intelligence Directorate. The Intercept is publishing the articles in redacted form as part of an ongoing project to release material from the files provided by NSA whistleblower Edward Snowden.
In addition to the aforementioned highlights, summarized in further detail below, the documents show how the NSA greatly expanded a secret eavesdropping partnership with Ethiopia’s draconian security forces in the Horn of Africa, as detailed in an investigation by longtime Intercept contributor Nick Turse. They describe the NSA’s operations at a base in Digby, England, where the agency worked with its British counterpart GCHQ to help direct drones in the Middle East and tap into communications through the Arab Spring uprisings, according to a separate article by Intercept reporter Ryan Gallagher. And they show how the NSA and GCHQ thwarted encryption systems used to protect peer-to-peer file sharing through the apps Kazaa and eDonkey, as explained here by Intercept technologist Micah Lee.
NSA did not comment for this article.
…
If you are interested in reporting based on redacted versions of twelve year old news (last half of 2005), this is the article for you.
The authors proclaim self-censorship and privilege saying:
…
The Intercept is publishing the articles in redacted form as part of an ongoing project to release material from the files provided by NSA whistleblower Edward Snowden.
…
These authors can milk their treasure trove of unredacted SIDreports, giving them an obvious advantage over other journalists.
Not as great an advantage as being white and male but it is a privilege unrelated to merit, one violates any concept of equal access.
Other reporters or members of the public notice connections unseen by the Intercept authors.
We won’t ever know since the Intercept, along with other media outlets, is quick to call foul on the privileges of others while clinging to its own.
PS: The lack of efforts by intelligence agencies to stop the SIDtoday series is silent testimony to its lack of importance. The SIDtoday series is little better than dated office gossip and not a complete (redacted) account of the same.
Meaningful intelligence reporting derails initiatives, operations, exposes criminal excesses with named defendants and holds the intelligence community accountable to the public. Not to be confused with the SIDtoday series and its like.
August 2, 2017
Potential NSA Leak Stream
The Government Accounting Office (GAO) has publicly identified a potential source of NSA technology leaks. The cumbersome title: DOD’s Monitoring of Progress in Implementing Cyber Strategies Can Be Strengthened (GAO-17-512) begins with this summary:
Officials from Department of Defense (DOD) components identified advantages and disadvantages of the “dual-hat” leadership of the National Security Agency (NSA)/Central Security Service (CSS) and Cyber Command (CYBERCOM) (see table). Also, DOD and congressional committees have identified actions that could mitigate risks associated with ending the dual-hat leadership arrangement, such as formalizing agreements between NSA/CSS and CYBERCOM to ensure continued collaboration, and developing a persistent cyber training environment to provide a realistic, on-demand training capability. As of April 2017, DOD had not determined whether it would end the dual-hat leadership arrangement.
…
At first I thought it said “ass-hat” leadership and went back to check. 😉
You can read the recommendations if you are in charge of improving that situation (an unlikely outcome) or take the GAO at its word as a place to mine for leaks.
Are dual-hat arrangements “leak patterns” much like “design patterns” in programming languages?
I ask because identifying “leak patterns,” whether in software (buffer overflows) or recurrent organizational security failures, could be a real boon to hounds and hares alike.
June 9, 2017
Real Talk on Reality (Knowledge Gap on Leaking)
Real Talk on Reality : Leaking is high risk by the grugq.
From the post:
On June 5th The Intercept released an article based on an anonymously leaked Top Secret NSA document. The article was about one aspect of the Russian cyber campaign against the 2016 US election — the targeting of election device manufacturers. The relevance of this aspect of the Russian operation is not exactly clear, but we’ll address that in a separate post because… just hours after The Intercept’s article went live the US Department of Justice released an affidavit (and search warrant) covering the arrest of Reality Winner — the alleged leaker. Let’s look at that!
…
You could teach a short course on leaking from this one post but there is one “meta” issue that merits your attention.
The failures of Reality Winner and the Intercept signal users need educating in the art of information leaking.
With wide spread tracking of web browsers, training on information leaking needs to be pushed to users. It would stand out if one member of the military requested and was sent an email lesson on leaking. An email that went to everyone in a particular command, not so much.
Public Service Announcements (PSAs) in web zines, as ads, etc. with only the barest of tips, is another mechanism to consider.
If you are very creative, perhaps “Mr. Bill” claymation episodes with one principle of leaking each? Need to be funny enough that viewing/sharing isn’t suspicious.
Other suggestions?
June 2, 2017
Unknown Buyers + Unknown Sellers ~= Closed Source Software
TurkuSec Community reports another collaborative effort to buy into the Shadow Brokers malware-of-the-month club:
“What Could Go Wrong?” is a valid question.
On the other hand, you are already spending $billions on insecure software every year.
Most of which is closed-source, meaning it may contain CIA/NSA backdoors.
A few hires in the right places and unbeknownst to the vendor, they would be distributing CIA/NSA malware.
If you credit denials of such activities by the CIA/NSA or any other government spy agency, you should stop using computers. You are a security risk to your employer.
A Shadow Brokers subscription, where 2,500 people risk $100 each for each release, on the other hand, is far safer than commercial software. If the the first release prove bogus, don’t buy a second one.
Contrast that with insecure closed source software for an OS or database that may contain CIA/NSA/etc. backdoors. You don’t get to avoid the second purchase. (You bought the maintenance package too. Am I right?)
I can’t and won’t counsel anyone to risk more than $100, but shared risk is the fundamental principle of insurance. Losses can and will happen. That’s why we distribute the risk.
That link again: https://t.co/wjMn3DjzQp.
PS: Shadow Brokers: Even a list of the names with brief descriptions might help attract people who want to share the risk of subscribing. The “big” corporations are likely too arrogant to think they need the release.
May 30, 2017
Crowd-Funding Public Access to NSA Tools!
Awesome! (with a caveat below)
Shadow Brokers Response Team is creating open & transparent crowd-funded analysis of leaked NSA tools.
The group calling itself the Shadow Brokers have released several caches of exploits to date. These caches and releases have had a detrimental outcome on the Internet at large, one leak especially resulted in the now in-famous WannaCry ransomware worm – others have been used by criminal crackers to illegally access infrastructure. Many have been analysing the data to determine its authenticity and impact on infrastructure, as a community it has been expressed that the harm caused by exploits could have been mitigated against had the Shadow Brokers been paid for their disclosures.
The leaks of information seen so far have included weaponized reliable exploits for the following platforms:
- Cisco
- Juniper
- Solaris
- Microsoft Windows
- Linux
The Shadow Brokers have announced they are offering a “monthly dump” service which requires a subscription of 100 ZCASH coins. Currently this is around £17688.29 but could change due to the fleeting nature of cryptocurrency. By paying the Shadow Brokers the cash they asked for we hope to pool resources and avert any future WannaCry type incidents. This patreon is a chance for those who may not have large budgets (SME, startups and individuals) in the ethical hacking and whitehat community to pool resources and buy a subscription for the new monthly released data.
The goal here is to raise sufficient funds from interested parties to purchase a subscription to the new data leak. We are attempting to perform the following task:
- Raise funds to purchase 100 ZCASH coins
- Purchase 100 ZCASH coins from a reputable exchange
- Transfer 100 ZCASH coins to ShadowBrokers with email address
- Access the data from the ShadowBrokers and distribute to backers
- Perform analysis on data leak and ascertain risk / perform disclosures
The Shadow Brokers have implied that the leak could be any of the following items of interest:
- web browser, router, handset exploits and tools
- newer material from NSA ops disk including Windows 10 exploits
- misc compromised network data (SWIFT or Nuclear programmes)
… (emphasis in original)
An almost excellent plan that with enough contributors, reduces the risk to any one person to a manageable level.
Two-hundred and fifty contributors at $100 each, makes the $25,000 goal. That’s quite doable.
My only caveat is the “…whitehat ethical hacker…” language for sharing the release. Buying a share in the release should be just that, buying a share. What participants do or don’t do with their share is not a concern.
Kroger clerks don’t ask me if I am going to use flour to bake bread for the police and/or terrorists.
Besides, the alleged NSA tools weren’t created by “…whitehat ethical hackers….” Yes? No government has a claim on others to save them from their own folly.
Any competing crowd-funded subscriptions to the Shadow Brokers release?
May 23, 2017
China Draws Wrong Lesson from WannaCry Ransomware
Chinese state media says US should take some blame for cyberattack
From the post:
…
China’s cyber authorities have repeatedly pushed for what they call a more “equitable” balance in global cyber governance, criticizing U.S. dominance.The China Daily pointed to the U.S. ban on Chinese telecommunication provider Huawei Technologies Co Ltd, saying the curbs were hypocritical given the NSA leak.
Beijing has previously said the proliferation of fake news on U.S. social media sites, which are largely banned in China, is a reason to tighten global cyber governance.
The newspaper said that the role of the U.S. security apparatus in the attack should “instill greater urgency” in China’s mission to replace foreign technology with its own.
The state-run People’s Daily compared the cyber attack to the terrorist hacking depicted in the U.S. film “Die Hard 4”, warning that China’s role in global trade and internet connectivity opened it to increased risks from overseas.
…
China is certainly correct to demand a place at the table for China and other world powers in global cyber governance.
But China is drawing the wrong lesson from the WannaCry ransomeware attacks if that is used as a motivation for closed source Chinese software to replace “foreign” technology.
NSA staffers may well be working for Microsoft and/or Oracle, embedding NSA produced code in their products. With closed source code, it isn’t possible to verify the absence of such code or to prevent its introduction.
Sadly, the same is true if closed source code is written by Chinese programmers, some of who may have agendas, domestic or foreign, of their own.
The only defense to rogue code is to invest in open source projects. Not everyone will read every line of code but being available for being read, is a deterrent to obvious subversion of an applications security.
China should have “greater urgency” to abandon closed source software, but investing in domestic closed source only replicates the mistake of investing in foreign closed source software.
Opensource projects cover every office, business and scientific need.
Chinese government support for Chinese participation in existing and new opensource projects can make these projects competitors to closed and potential spyware products.
The U.S. made the closed source mistake for critical cyber infrastructure. China should not make the same mistake.
May 21, 2017
More Dicking With The NSA
Privacy-focused Debian 9 ‘Stretch’ Linux-based operating system Tails 3.0 reaches RC status by
From the post:
If you want to keep the government and other people out of your business when surfing the web, Tails is an excellent choice. The Linux-based operating system exists solely for privacy purposes. It is designed to run from read-only media such as a DVD, so that there are limited possibilities of leaving a trail. Of course, even though it isn’t ideal, you can run it from a USB flash drive too, as optical drives have largely fallen out of favor with consumers.
Today, Tails achieves an important milestone. Version 3.0 reaches RC status — meaning the first release candidate (RC1). In other words, it may soon be ready for a stable release — if testing confirms as much. If you want to test it and provide feedback, you can download the ISO now.
…
Fagioli covers some of the details but the real story is this:
The sooner testers (that can include you) confirm the stability, etc., of Tails Version 3.0 (RC1), the sooner it can be released for general use.
In part, the release schedule for Tails Version 3.0 (RC1) depends on you.
Your response?
Check Fagoli’s post for links to the release and docs.
May 18, 2017
How To Legally Dick With The NSA – PostgreSQL 10 Beta 1
The release of PostgreSQL 10 Beta 1 gives everyone an opportunity to legally dick with the NSA.
In Stop Blaming NSA For The Ransomware Attack, Patrick Tucker repeats claims by the NSA that about 80% of vulnerabilities are revealed and 20% are concealed by the NSA.
Which means if there are 10 security vulnerabilities in PostgreSQL 10 Beta 1, the NSA will keep two for themselves.
Let’s disappoint them on that score. With widespread community testing, fuzzing, etc., the NSA score on PostgreSQL 10 Beta 1 could be zero.
That won’t help vendors with 70 million lines of closed source databases (look for Mary Ann Davidson). Such databases may have true accidental vulnerabilities or ones introduced by NSA ringers.
If NSA ringers working for closed source companies sounds like tin-hat conspiracy theory, recall the NSA is barred from spying on American citizens at all. In fact, they have vehemently denied it. At least until they admitted they were lying and in fact spying on all American citizens.
Also bear in mind that the NSA was a participant in many of the covert/overt attempts by the United States to influence elections in other countries. (Dov H. Levin, as of May 18, 2017, the datasets are forthcoming. See also: Database Tracks History Of U.S. Meddling In Foreign Elections, an NPR interview that counts 80 US-backed efforts to interfere in elections.)
On the technical front, the NSA is known to have intentionally damaged a U.S. cryptography standard. NSA Efforts to Evade Encryption Technology Damaged U.S. Cryptography Standard. That report isn’t from a blog that is a continuation of a photocopied version of a mimeographed conspiracy report found in low-end coffee shops.
No, the damage to U.S. cryptography report appears in Scientific American.
I can’t honestly name one illegal, immoral, unethical, act that the NSA is not capable of.
You?
Beyond “sticking to the NSA,” database researchers and users have these PostgreSQL 10 Beta 1 features to enjoy:
The PostgreSQL Global Development Group announces today that the first beta release of PostgreSQL 10 is available for download. This release contains previews of all of the features which will be available in the final release of version 10, although some details will change before then. Users are encouraged to begin testing their applications against this latest release.
Major Features of 10
The new version contains multiple features that will allow users to both scale out and scale up their PostgreSQL infrastructure:
- Logical Replication: built-in option for replicating specific tables or using replication to upgrade
- Native Table Partitioning: range and list partitioning as native database objects
- Additional Query Parallelism: including index scans, bitmap scans, and merge joins
- Quorum Commit for Synchronous Replication: ensure against loss of multiple nodes
We have also made three improvements to PostgreSQL connections, which we are calling on driver authors to support, and users to test:
- SCRAM Authentication, for more secure password-based access
- Multi-host “failover”, connecting to the first available in a list of hosts
- target_session_attrs parameter, so a client can request a read/write host
Additional Features
Many other new features and improvements have been added to PostgreSQL 10, some of which may be as important, or more important, to specific users than the above. Certainly all of them require testing. Among them are:
- Crash-safe and replicable Hash Indexes
- Multi-column Correlation Statistics
- New “monitoring” roles for permission grants
- Latch Wait times in pg_stat_activity
- XMLTABLE query expression
- Restrictive Policies for Row Level Security
- Full Text Search support for JSON and JSONB
- Compression support for pg_receivewal
- ICU collation support
- Push Down Aggregates to foreign servers
- Transition Tables in trigger execution
Further, developers have contributed performance improvements in the SUM() function, character encoding conversion, expression evaluation, grouping sets, and joins against unique columns. Analytics queries against large numbers of rows should be up to 40% faster. Please test if these are faster for you and report back.
See the Release Notes for a complete list of new and changed features.
…
Make the lives of PostgreSQL users everywhere better and the lives of government intelligence services around the world worse!
I call that a win-win situation.
May 17, 2017
Don’t Blame NSA For Ransomware Attack!
Stop Blaming NSA For The Ransomware Attack by Patrick Tucker.
Most days I think the NSA should be blamed for everything from global warming to biscuits that fail to rise.
But for leaked cyber weapons? No blame whatsoever.
Why? The answer lies in the NSA processing of vulnerabilities.
From the post:
…
“You’ve heard my deputy director say that in excess of 80-something percent of the vulnerabilities are actually disclosed—responsibly disclosed —to the vendors so that they can then actually patch and remediate for that,” Curtis Dukes, NSA’s former deputy national manager for national security systems, said at an American Enterprise Institute event in October. “So I do believe it’s a thoughtful process that we have here in the U.S.”Dukes said the impetus to conceal an exploit vanishes when it is used by a criminal gang, adversarial nation, or some other malefactor.
We may choose to restrict a vulnerability for offensive purposes, like breaking into an adversary’s network, he said. But that doesn’t mean we’re not also constantly looking for signs whether another nation-state or criminal network has actually found that same vulnerability and now are using it. As soon as we see any indications of that, then that decision immediately flips, and we move to disseminate and remediate.
…
You may think that is a “thoughtful process” but that’s not why I suggest the NSA should be held blameless.
Look at the numbers on vulnerabilities:
80% disclosed by the NSA for remediation.
20% concealed by the NSA.
Complete NSA disclosure means the 20% now concealed, vanishes for everyone.
That damages everyone seeking government transparency.
Don’t wave your arms in the air crying “ransomware! ransomeware! Help me! Help me!,” or “Blame the NSA! “Blame the NSA.”
Use FOIA requests, leaks and cyber vulnerabilities to peel governments of their secrecy, like lettuce, one leaf at a time.
May 16, 2017
Correction to Financial Times on EsteemAudit
Hackers prime second classified US cyber weapon by Sam Jones and Max Seddon.
From the post:
Criminal hacking groups have repurposed a second classified cyber weapon stolen from US spies and have made it available on the so-called dark web after the success of the WannaCry attack that swept across the globe on Friday.
The hacking tool, developed by the US National Security Agency and called EsteemAudit, has been adapted and is now available for criminal use, according to security analysts.
…
Correction:
“…is now available for criminal use…” should read:
“…is now available for widespread criminal use….”
NSA cyber weapons have always in use by criminals. The debate now is over more criminals using the same weapons.
If those weapons are used against the NSA and its co-conspirators, I don’t see a problem.
Marketing Advice For Shadow Brokers
Shadow Brokers:
I read your post OH LORDY! Comey Wanna Cry Edition outlining your plans for:
In June, TheShadowBrokers is announcing “TheShadowBrokers Data Dump of the Month” service. TheShadowBrokers is launching new monthly subscription model. Is being like wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month. What members doing with data after is up to members.
TheShadowBrokers Monthly Data Dump could be being:
- web browser, router, handset exploits and tools
- select items from newer Ops Disks, including newer exploits for Windows 10
- compromised network data from more SWIFT providers and Central banks
- compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
More details in June.
OR IF RESPONSIBLE PARTY IS BUYING ALL LOST DATA BEFORE IT IS BEING SOLD TO THEPEOPLES THEN THESHADOWBROKERS WILL HAVE NO MORE FINANCIAL INCENTIVES TO BE TAKING CONTINUED RISKS OF OPERATIONS AND WILL GO DARK PERMANENTLY YOU HAVING OUR PUBLIC BITCOIN ADDRESS
… (emphasis in original)
I don’t know your background in subscription marketing but I don’t see Shadow Brokers as meeting the criteria for a successful subscription business. 9 Keys to Building a Successful Subscription Business.
Unless you want to get into a vulnerability as commodity business, with its attendant needs for a large subscriber base, advertising, tech support, etc., with every service layer adding more exposure, I just don’t see it. The risk of exposure is too great and the investment before profit too large.
I don’t feel much better about a bulk purchase from a major government or spy agency. The likely buyers already have the same or similar data so don’t have an acquisition motive.
Moreover, likely buyers don’t trust the Shadow Brokers. As a one time seller, Shadow Brokers could collect for the “lost data” and then release it for free in the wild.
You say that isn’t the plan of Shadow Brokers, but likely buyers are untrustworthy and expect the worst of others.
If I’m right and traditional subscription and/or direct sales models aren’t likely to work, that doesn’t mean that a sale of the “lost data” is impossible.
Consider the Wikileak strategy with the the Podesta emails.
The Podesta emails were replete with office chatter, backbiting remarks, and other trivia.
Despite the lack of intrinsic value, their importance was magnified by the release of small chunks of texts, each of which might include something important.
With each release, main stream media outlets such as the New York Times, the Washington Post, and others went into a frenzy of coverage.
That was non-technical data so a similar strategy with “lost data” will require supplemental, explanatory materials for the press.
Dumping one or two tasty morsels every Friday, for example, will extend media coverage, not to mention building public outrage that could, no guarantees, force one or more governments to pony up for the “lost data.”
Hard to say unless you try.
PS: For anyone who thinks this post runs afoul of “aiding hackers” prohibitions, you have failed to consider the most likely alternate identity of Shadow Brokers, that of the NSA itself.
Ask yourself:
Who wants real time surveillance of all networks? (NSA)
What will drive acceptance of real time surveillance of all networks? (Hint, ongoing and widespread data breaches.)
Who wants to drive adoption of Windows 10? (Assuming NSA agents wrote backdoors into the 50 to 60 million lines of code in Windows 10.)
Would a government that routinely assassinates people and overthrows other governments hesitate to put ringers to work at Microsoft? Or other companies?
Is suborning software verboten? (Your naiveté is shocking.)
May 12, 2017
WanaCrypt0r: The Wages Of False Economy
Malware that attacks unsupported or unpatched Microsoft software started making the rounds today.
Just some of the coverage:
Malware Stolen From The NSA Cripples Computers In 74 Countries (And Counting)
Massive ransomware cyber-attack hits computers in 74 countries
Cyber-attack hits 74 countries with UK hospitals among targets – live updates
Cyberattack Hits Dozen Nations ‘Using Leaked NSA Hacking Tool’
Massive ransomware attack hits 99 countries
Criminals used leaked NSA cyberweapon in crippling ransomware attack, experts say
Global cyberattack disrupts shipper FedEx, UK health system
Hackers use leaked NSA bug in massive global cyber attack
Wanna Decrypter 2.0 ransomware attack: what you need to know
Wana Decrypt0r Ransomware Using NSA Exploit Leaked by Shadow Brokers Is on a Rampage
You will see phrases like “weapons grade malware,” “NSA exploit,” “NSA cyberweapon,” etc., and many others over the coming days.
It will be mentioned but few consequences will be seen for managers who practiced false economy, in not upgrading their Microsoft systems in a timely fashion.
It is equally unlikely that sysadmins will suffer for their failure to patch currently supported Microsoft systems in a timely manner.
Given those two likely outcomes, the next “massive global cyber attack,” is a question of when, not if. Managers will continue to practice false economies and sysadmins won’t follow good patching practices.
My suggestions:
- Upgrade to supported Microsoft software.
- Implement and audit patch application.
- Buy Microsoft stock.
The first two will help keep you safe and the third one will enable you to profit from the periodic panics among unsupported Microsoft software users.
May 6, 2017
Introduction: The New Face of Censorship
Introduction: The New Face of Censorship by Joel Simon.
From the post:
In the days when news was printed on paper, censorship was a crude practice involving government officials with black pens, the seizure of printing presses and raids on newsrooms. The complexity and centralization of broadcasting also made radio and television vulnerable to censorship even when the governments didn’t exercise direct control of the airwaves. After all, frequencies can be withheld; equipment can be confiscated; media owners can be pressured.
New information technologies–the global, interconnected internet; ubiquitous social media platforms; smart phones with cameras–were supposed to make censorship obsolete. Instead, they have just made it more complicated.
Does anyone still believe the utopian mantras that information wants to be free and the internet is impossible to censor or control?
The fact is that while we are awash in information, there are tremendous gaps in our knowledge of the world. The gaps are growing as violent attacks against the media spike, as governments develop new systems of information control, and as the technology that allows information to circulate is co-opted and used to stifle free expression.
…
The work of Joel Simon and the Committee to Protect Journalists is invaluable. The challenges, dangers and hazards for journalists around the world are constant and unrelenting.
I have no doubt about Simon’s account of suppression of journalists. His essay is a must read for everyone who opposes censorship, at least in its obvious forms.
A more subtle form of censorship is practiced in the United States, self-censorship.
How many stories on this theme have you read in the last couple of weeks? U.S. spy agency abandons controversial surveillance technique
Now, how many of those same stories mentioned that the NSA has a long and storied history of lying to the American public, presidents and congress?
By my count, which wasn’t exhaustive, the total is 0.
Instead of challenging this absurd account, Reuters reports the NSA reports as though it were true and fails to remind the public it is relying on a habitual liar.
Show of hands, how many readers think the Reuters staff forgot that the NSA is a hotbed of liars and cheats?
There is little cause for government censorship of US media outlets. They censor themselves before the government can even ask.
Support the Committee to Protect Journalists and perhaps their support of journalists facing real censorship will shame US media into growing a spine.
April 24, 2017
Leaking Improves Security – Secrecy Weakens It
If you need a graphic for the point that leaking improves security – secrecy weakens it, consider this one:
Ask your audience:
Prior to the Shadow Brokers leak of the NSA’s DoublePulsar Malware, how many people were researching a counter to it?
Same question, but substitute: After the Shadow Brokers leak ….
As the headline says: Leaking Improves Security – Secrecy Weakens It.
Image originates from: Over 36,000 Computers Infected with NSA’s DoublePulsar Malware by Catalin Cimpanu.
Anyone who suggests otherwise wants you and others to be insecure.
April 20, 2017
Leak “Threatens Windows Users Around The World?”
Leaked NSA Malware Threatens Windows Users Around The World? by Sam Biddle.
Really? Shadow Brokers leaking alleged NSA malware “threatens users around the world?”
Hmmm, I would think that the NSA developing Windows malware is what threatens users around the world.
Yes?
Unlike the apparent industry concealment of vulnerabilities, the leaking of NSA malware puts all users on an equal footing with regard to those vulnerabilities.
In a phrase, users are better off for the NSA malware leak than they were before.
They know (or at least it has been alleged) that these leaked vulnerabilities have been patched in supported Microsoft products. By upgrading to those products, they can avoid these particular pieces of NSA malware.
Leaking vulnerabilities enables users to avoid perils themselves, in this case by upgrading, and/or to demand patches from vendors responsible for the vulnerabilities.
Do you see a downside I don’t?
Well, aside from trashing the market for vulnerabilities and gelding security agencies, neither one of which I will lose any sleep over.
November 21, 2016
OPM Farce Continues – 2016 Inspector General Report
U.S. Office of Personnel Management – Office of the Inspector General – Office of Audits
The Office of Personnel Management hack was back in the old days when China was being blamed for every hack. There’s no credible evidence of that but the Chinese were blamed in any event.
The OMP hack illustrated the danger inherent in appointing campaign staff to run mission critical federal agencies. Just a sampling of the impressive depth of Archuleta’s incompetence, read Flash Audit on OPM Infrastructure Update Plan.
The executive summary of the current report offers little room for hope:
This audit report again communicates a material weakness related to OPM’s Security Assessment and Authorization (Authorization) program. In April 2015, the then Chief Information Officer issued a memorandum that granted an extension of the previous Authorizations for all systems whose Authorization had already expired, and for those scheduled to expire through September 2016. Although the moratorium on Authorizations has since been lifted, the effects of the April 2015 memorandum continue to have a significant negative impact on OPM. At the end of fiscal year (FY) 2016, the agency still had at least 18 major systems without a valid Authorization in place.
However, OPM did initiate an “Authorization Sprint” during FY 2016 in an effort to get all of the agency’s systems compliant with the Authorization requirements. We acknowledge that OPM is once again taking system Authorization seriously. We intend to perform a comprehensive audit of OPM’s Authorization process in early FY 2017.
This audit report also re-issues a significant deficiency related to OPM’s information security management structure. Although OPM has developed a security management structure that we believe can be effective, there has been an extremely high turnover rate of critical positions. The negative impact of these staffing issues is apparent in the results of our current FISMA audit work. There has been a significant regression in OPM’s compliance with FISMA requirements, as the agency failed to meet requirements that it had successfully met in prior years. We acknowledge that OPM has placed significant effort toward filling these positions, but simply having the staff does not guarantee that the team can effectively manage information security and keep OPM compliant with FISMA requirements. We will continue to closely monitor activity in this area throughout FY 2017.
It’s illegal but hacking the OPM remains easier than the NSA.
Hacking the NSA requires a job at Booz Allen and a USB drive.
November 2, 2016
Is Google Fancy Bear? Or is Microsoft? Factions of Fancy Bear?
Fancy Bear: Russia-linked hackers blamed for exploiting Windows zero-day flaw.
From the post:
MICROSOFT IS USING a new tactic to get people to upgrade to Windows 10 by warning that those who don’t could fall victim to Russian hackers.
The company said in a security advisory that a hacking group previously linked to the Russian government and US political hacks has exploited a newly discovered Windows zero-day flaw that was outed by Google earlier this week.
Microsoft claimed that the hacking group ‘Strontium’, more commonly known as ‘Fancy Bear’, had carried out a small number of attacks using spear phishing techniques.
…
Too much of a coincidence Google drops a zero-day flaw the same week it shows up in the wild from Fancy Bear?
Too much of a coincidence Windows 10 is the magic solution to an “all Windows/all the time” vulnerability?
Could Google and Microsoft be rival factions of Fancy Bear?
The super-hackers in North Korea, should be offended by the obsession with Fancy Bear. Double ditto for the Chinese warlord class hackers.
For months, years in internet time, it’s Fancy Bear this and Fancy Bear that. Your toaster on the blink, must be Fancy Bear. Your printer is jammed, must be Fancy Bear. Worried about hacking paper ballots? Must be Fancy Bear.
Despite DNI James Clapper‘s paranoid and Hillary Clinton-serving fantasies, there is more to attribution than saying a catchy name.
November 1, 2016
What’s Your NSA Number?
You have heard of Erdös numbers, which are based on collaboration of mathematicians with Paul Erdös. The Erdös Number Project
The publication of (alleged) NSA hacked sites may give rise to your NSA Number. (New leak may show if you were hacked by the NSA by Dan Goodin.)
With two assumptions:
- The 290 IP addresses are indeed valid.
- The NSA did in fact hack those sites.
The top NSA Number would be 290. (I combined, sorted and deduped the IP addresses. Other counts are out there but I don’t know how they were made.)
As a first step, I ran ping on the 290 and 74 reported as “up.”
Many others avenues of server detection to pursue but a common list is a good start.
Edits/changes to my list?
Thanks!
September 20, 2016
Betraying Snowden:… [Cynical, but not odd]
Betraying Snowden: There’s a special place in journalism hell for The Washington Post editorial board by Daniel Denvir.
From the post:
There is a special place in journalism hell reserved for The Washington Post editorial board now that it has called on President Barack Obama to not pardon National Security Agency whistleblower Edward Snowden.
As Glenn Greenwald wrote, it’s an odd move for a news publication, “which owes its sources duties of protection, and which — by virtue of accepting the source’s materials and then publishing them — implicitly declares the source’s information to be in the public interest.” Notably, the Post decided to “inexcusably omit . . . that it was not Edward Snowden, but the top editors of the Washington Post who decided to make these programs public,” as Greenwald added.
The Post’s peculiar justification is as follows: While the board grudgingly conceded that reporters, thanks to Snowden, revealed that the NSA’s collection of domestic telephone metadata — which “was a stretch, if not an outright violation, of federal surveillance law” — it condemns him for revealing “a separate overseas NSA Internet-monitoring program, PRISM, that was both clearly legal and not clearly threatening to privacy.”
…
Washington Post opposition to a pardon for Edward Snowden isn’t odd at all.
Which story generates more PR for the Washington Post:
- The Washington Post, having won a Pulitzer prize due to Edward Snowden, joins a crowd calling for his pardon?
- The Washington Post, having won a Pulitzer prize due to Edward Snowden, opposes his being pardoned?
It’s not hard to guess which one generates more ad-views and therefore the potential for click-throughs.
I have no problems with the disclosure of PRISM, save for Snowden having to break his word as a contractor to keep his client’s secrets, well, secret.
No one could be unaware that the NSA engages in illegal and immoral activity on a daily basis before agreeing to be employed by them.
Although Snowden has done no worse than his former NSA employers, it illustrates why I have no trust in government agencies.
If they are willing to lie for what they consider to be “good” reasons to you, then they are most certainly willing to lie to me.
Once it is established that an agency, take the NSA for example, has lied on multiple occasions, on what basis would you trust them to be telling the truth today?
Their assurance, “we’re not lying this time?” That seems rather tenuous.
Same rule should apply to contractors who lie to or betray their clients.
August 15, 2016
Hackers Say They Hacked NSA-Linked Group… (Fact or Fantasy?)
Hackers Say They Hacked NSA-Linked Group, Want 1 Million Bitcoins to Share More by Lorenzo Franceschi-Biccierai.
From the post:
A mysterious hacker or hackers going by the name “The Shadow Brokers” claims to have hacked a group linked to the NSA and dumped a bunch of its hacking tools. In a bizarre twist, the hackers are also asking for 1 million bitcoin (around $568 million) in an auction to release more files.
“Attention government sponsors of cyber warfare and those who profit from it!!!!” the hackers wrote in a manifesto posted on Pastebin, on GitHub, and on a dedicated Tumblr. “How much you pay for enemies cyber weapons? […] We find cyber weapons made by creators of stuxnet, duqu, flame.”
The hackers referred to their victims as the Equation Group, a codename for a government hacking group widely believed to be the NSA.
…
What is the first thing that strikes you as dodgy about this claimed hack?
If you had a hacking weapons from the NSA, wouldn’t you first approach other national governments?
The NSA would still hear about it but the buyers would be doing their best to keep sale and hack secret as well.
Here? The alleged hackers have painted a target on their backs and “chump” on anyone who parts with any bitcoins for a release of the alleged weapons.
The best to hope for is the alleged hackers aren’t prosecuted for fraud as a result of any online auction.
They shouldn’t be. Buying allegedly stolen property and being cheated isn’t a crime, it’s a valuable lesson.
August 6, 2016
No ‘Raiders of the Lost Ark’ Stockpile? You Are Still In Danger!
NSA denies ‘Raiders of the Lost Ark’ stockpile of security vulnerabilities by Alex Hern.
From the post:
America’s National Security Agency (NSA) spends upwards of $25m in a year buying previously undisclosed security vulnerabilities – known as zero days, because that’s the length of time the target has had to fix them – but the large investment may not result in as much of a collection of hacking capabilities as is widely assumed.
Jason Healey, a senior research scholar at Columbia University and director at the Atlantic Council policy thinktank, argues that the true number of zero days stockpiled by the NSA is likely in the “dozens”, and that the agency only adds to that amount by a very small amount each year. “Right now it looks like single digits,” he says, adding that he has “high confidence in this assessment.”
…
One key piece of evidence comes from the NSA itself, which in 2015 claimed that 91% of vulnerabilities it procured were eventually disclosed to the vendors whose products were at risk. Of the other 9%, at least some of those weren’t disclosed because they were fixed before they could be, the agency adds.
Similarly, the White House has revealed that in one year since the current disclosure policy was implemented, it reviewed about 100 software vulnerabilities discovered by the NSA to determine if they should be disclose, and “kept only about two”. Healey adds that in the autumn of 2014, he was personally told that every single vulnerability which had come up for review had been disclosed.
…
No amount of factual reporting is likely to dispel the myth of an NSA horde of zero days.
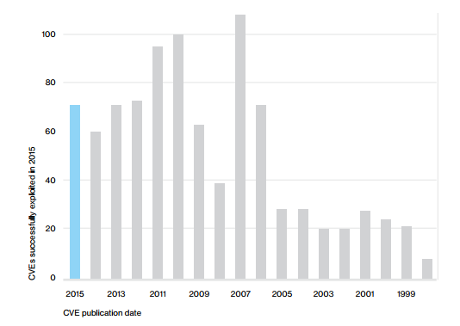
However, the Verizon 2016 Data Breach Investigations Report makes it clear that zero days aren’t the main source of hacking danger:
That’s not an error! Vulnerabilities prior to 1999 are still in use.
You can spend your days discussing rumors of the latest zero day or you can insist that IT follow a verified application of patches process.
How effective is patching known vulnerabilities?
The top 10 internal vulnerabilities accounted for over 78 percent of all internal vulnerabilities during 2015. All 10 internal vulnerabilities are directly related to outdated patch levels on the target systems. (2016 NTT Group, Global Threat Intelligence Report, page 5. Emphasis in original.)
Routine patching can reduce your internal vulnerabilities by 78% (on average).
That’s a clear, actionable, measurable requirement.
Call up your IT department, ask for a list of all the software in your enterprise and a list of patches that have been applied to each instance and those waiting to be applied (as per the vendor).
Remember, a data breach maybe ITs “fault,” but it may be your job that is at risk.
PS: One of earliest uses of topic maps was to track software on a university network.
August 4, 2016
Anonymous Video – USA -> NSA
While amusing, the topic of this video is deadly serious.
The NSA, firmly, albeit misguidedly, believes:
The United States today faces very real, very grave national security threats. Extremism and international terrorism flourish in too many areas of the world, threatening our warfighters, our allies and our homeland. Regional conflicts can have serious effects on U.S. national interests. Hostile foreign governments and terrorists trade in, or seek to acquire, weapons of mass destruction and/or the materials to produce them. Tons of illegal drugs are smuggled into our country each year.
The newest threats we face, and perhaps the fastest growing, are those in cyberspace. Cyber threats to U.S. national and economic security increase each year in frequency, scope and severity of impact. Cyber criminals, hackers and foreign adversaries are becoming more sophisticated and capable every day in their ability to use the Internet for nefarious purposes.
As a nation, we are dependent on the Internet – we use it for everything. We communicate online, bank and shop online, and store much of our personal information there. In business, education and government, we all count on having ready access to the Internet and its many capabilities as we go about our daily routines. The Internet opens up new worlds to users.
But while cyberspace offers great opportunities, it also comes with vulnerabilities. Our information networks and technology are constantly at risk from a variety of bad actors using a multitude of techniques – remote hacking intrusions, the placement of malware, spearphishing and other means of gaining access to networks and information.
Some of these bad actors are criminals motivated by profit, particularly in the areas of identity theft and other forms of financial cybercrime. The cost of cybercrime – already in the billions of dollars – rises each year.
But cyber threats also come from nation states and other actors who seek to exploit information to gain an advantage over the United States. They might seek an economic advantage, or to gain insight into our military or foreign policy. Denial of service attacks disrupt business and undermine confidence.
Terrorists and extremist groups today use the power of the Internet, especially social media, to spread their messages of hate and intolerance, and to recruit new members, often targeting vulnerable young people. The global reach of cyberspace and the complexity of its networks provide bad actors ample places to hide, safe from the reach of international law.
To meet these threats, our national leaders, military leaders, policy makers and law enforcement personnel must understand who our adversaries are, where they are, and what their capabilities, plans and intentions are. At the same time, we must ensure that we protect our own national security information from those who would do us harm. These are the capabilities that the National Security Agency provides to our nation, to our leaders and to our fellow Americans – 24 hours a day, seven days a week. [Understanding The Threat]
Surrounded by jinns and demons, known and unknown, as the only hope for Truth, Justice and the American Way, what choice does the NSA have but to use any and all means, fair and foul, to meet those threats?
As you know, I’m not a big fan of the NSA or its surveillance programs, but in researching this post, I encountered a shift in the rhetoric of the NSA.
As you can see in Understanding The Threat, the entire focus is on hazards and dangers that would justify any degree of action of lawlessness.
Contrast that with the Commitment that is preserved by the Internet Archive (December, 2015):
These are our commitments to you, our fellow citizens:
- We will act with integrity to advance the rights, goals, and values of the Nation.
- We will adhere to the spirit and the letter of the Constitution and the laws and regulations of the United States.
- We will support and protect our troops in the field.
- We will combat terrorism around the globe – when necessary, putting our lives on the line to preserve the Nation.
- We will provide our policymakers, negotiators, ambassadors, law enforcement community, and military the vital intelligence they need to protect and defend the Nation.
- We will defend the national security networks vital to our Nation.
- We will be a trusted steward of public resources and place prudent judgment over expediency.
- We will continually strive for transparency in all our review, monitoring, and decision-making processes.
- We will be accountable for our actions and take responsibility for our decisions.
- We will honor Open Government and Transparency mandates by making timely and accurate information available to the public, subject to valid privacy, confidentiality, security or other restrictions under existing law and policies.
- Along with those exciting programs we partner with the Maryland STEM program.
What I find even more disturbing than the current threat statement is that it was written after mass collection of telephone data (under the Committment) was found to be useless:
A member of the White House review panel on NSA surveillance said he was “absolutely” surprised when he discovered the agency’s lack of evidence that the bulk collection of telephone call records had thwarted any terrorist attacks.
“It was, ‘Huh, hello? What are we doing here?’” said Geoffrey Stone, a University of Chicago law professor, in an interview with NBC News. “The results were very thin.”
While Stone said the mass collection of telephone call records was a “logical program” from the NSA’s perspective, one question the White House panel was seeking to answer was whether it had actually stopped “any [terror attacks] that might have been really big.”
“We found none,” said Stone.
Under the NSA program, first revealed by ex-contractor Edward Snowden, the agency collects in bulk the records of the time and duration of phone calls made by persons inside the United States.
Stone was one of five members of the White House review panel – and the only one without any intelligence community experience – that this week produced a sweeping report recommending that the NSA’s collection of phone call records be terminated to protect Americans’ privacy rights. (NSA program stopped no terror attacks, says White House panel member by Michael Isikoff.)
…
Shouldn’t the three hundred plus page report: Liberty and Security in a Changing World, dated 12 December 2013, result in a less paranoid, less extreme view of threats?
Pursuit of a paranoid and largely delusional view of the world, even post-exposure as paranoid and delusional, does not bode well for those subject to NSA surveillance.
Encrypt, Onionize and Erase (EOE) is your new mantra.
July 12, 2016
New Linux Journal Subscription Benefit!
Benefits of a Linux Journal subscription you already know:
- “Linux Journal, currently celebrating its 20th year of publication, is the original magazine of the global Linux community, delivering readers the advice and inspiration they need to get the most out of their Linux systems.”
- $29.50 (US) buys 12 issues and access to the Linux Journal archive.
- Linux Journal has columns written by regular columns written by Mick Bauer, Reuven Lerner, Dave Taylor, Kyle Rankin, Bill Childers, John Knight, James Gray, Zack Brown, Shawn Powers and Doc Searls.
- For more see the Linux Journal FAQ.
Now there is a new Linux Journal subscription benefit:
You are flagged as an extremist by the NSA
NSA Labels Linux Journal Readers and TOR and TAILS Users as Extremists by Dave Palmer.
End the constant worry, nagging anxiety, endless arguments with friends about who is being tracked by the NSA! For the small sum of $29.50 (US) you can buy your way into the surveillance list at the NSA.
I can’t think of a cheaper way to get on a watch list, unless you send threatening letters to the U.S. President, which is a crime, so don’t do it.
Step up and assume the mantle of “extremist” in the eyes of the NSA.
You would be hard pressed to find better company.
PS: Being noticed may not seem like a good idea. But the bigger the NSA haystack, the safer all needles will be.
June 8, 2016
Intelligence Suicide By Data
Facing Data Deluge, Secret U.K. Spying Report Warned of Intelligence Failure by Ryan Gallagher.
From the post:
…
The amount of data being collected, however, proved difficult for MI5 to handle. In March 2010, in another secret report, concerns were reiterated about the agency’s difficulties processing the material it was harvesting. “There is an imbalance between collection and exploitation capabilities, resulting in a failure to make effective use of some of the intelligence collected today,” the report noted. “With the exception of the highest priority investigations, a lack of staff and tools means that investigators are presented with raw and unfiltered DIGINT data. Frequently, this material is not fully assessed because of the significant time required to review it.”
…
Ironic this story appears less than two (2) weeks after reports of the FBI seeking NSL (national security letter) authority to obtain email records and browsing histories.
I should not complain about the FBI, NSA and other government agencies committing intelligence suicide by data.
Their rapidly growing ineffectiveness shields innocents from their paranoid fantasies.
At the same time, that ineffectiveness inhibits the performance of legitimate purposes. (The FBI, once upon a time, had a legitimate purpose, some of the others, well, that’s an issue for debate.)
So we are clear, I don’t consider contracts for “butts in seats” for either contractors or agencies to be for “legitimate purposes.” I reserve the phrase “legitimate purposes” for activities that further the stated goals of the agency, not padding staffing rolls, not occupying as much office space as possible, not having the most forms or whatever other criteria functions as the measure of success in a particular agency.
Hints for federal agencies already committing intelligence suicide by data or approaching that point:
- What data sources have proven valuable in the past? (Reminder: Phone metadata records have not. Not ever.)
- What data sources, in order of historical importance, are available in case X?
- Assemble the data from the top performing resources
For example, if an informant has direct contact with an alleged Islamic State supporter, isn’t that the best source of evidence for their plans and thinking? Do you really need their websearch history from an internet services provider? Considering that you will ask for everyone’s web search history to avoid disclosing the particular web history you are seeking.
To be sure, vendors will sell you as much data processing and storage capacity as you care to purchase, but you won’t be any closer to stopping terrorism. Just closer to the end of your budget for the current fiscal year.
Is intelligence suicide by data a goal of your agency?
May 16, 2016
Censored SIDtoday File Release
Snowden Archive — The SIDtoday Files
From the post:
The Intercept’s first SIDtoday release comprises 166 articles, including all articles published between March 31, 2003, when SIDtoday began, and June 30, 2003, plus installments of all article series begun during this period through the end of the year. Major topics include the National Security Agency’s role in interrogations, the Iraq War, the war on terror, new leadership in the Signals Intelligence Directorate, and new, popular uses of the internet and of mobile computing devices.
Along with this batch, we are publishing the stories featured below, which explain how and why we’re releasing these documents, provide an overview of SIDtoday as a publication, report on one especially newsworthy set of revelations, and round up other interesting tidbits from the files.
…
There are a series of related stories with this initial release:
The Intercept is Broadening Access to the Snowden Archive. Here’s Why by Glenn Greenwald.
NSA Closely Involved in Guantánamo Interrogations, Documents Show by Cora Currier.
The Most Intriguing Spy Stories From 166 Internal NSA Reports by Micah Lee, Margot Williams.
What It’s Like to Read the NSA’s Newspaper for Spies by Peter Maass.
How We Prepared the NSA’s Sensitive Internal Reports for Release by The Intercept.
A master zip file has all the SIDtoday files released thus far.
Comments on the censoring of these files will follow.
Twitter Giveth and Taketh Away (NSA as Profit Center?)
Twitter Giveth: GCHQ intelligence agency joins Twitter. Just about anyone can get a Twitter account these days.
Do see the GCHQ GitHub site for shared software.
Taketh Away Twitter Bars Intelligence Agencies From Using Analytics Service.
Twitter has barred Dataminr from providing services to government intelligence services.
Dataminr monitors the entire Twitter pipe and provides analytics based on that stream.
Will this result in the NSA sharing its signal detection in the Twitter stream with other intelligence agencies?
Or for that matter, the NSA could start offering commercial signal detection services across all its feeds. Make it a profit center for the government rather than a money pit.
BTW, don’t be deceived by the illusion of space between government and Twitter, or any other entity that cooperates with a national government. Take “compromised” as a given. The real questions are by who and for what purpose?