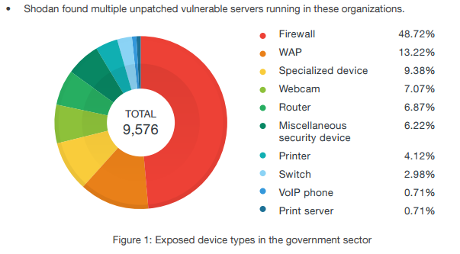
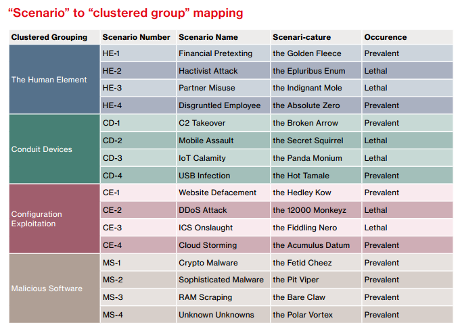
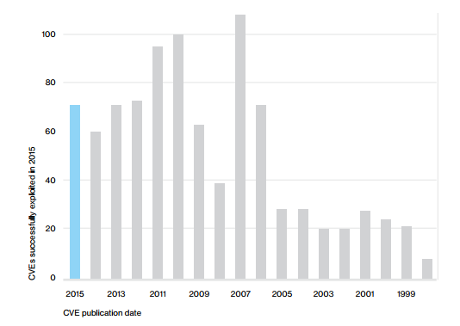
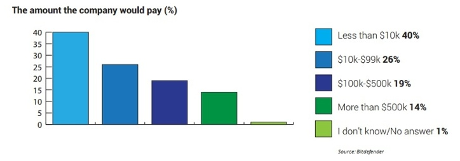
Letterlocking The technology of folding & securing an epistolary writing substrate to function as its own envelope.
From the about page:
Letterlocking – Unlocking History
Welcome to letterlocking! You can find essential information about letterlocking and the Unlocking History research team on this page. We will be updating the website regularly in the coming months, including major uploads to the Dictionary of Letterlocking (DoLL) – so please check in periodically, and follow us on social media for all the news.
Unlocking History
Unlocking History is the name for a group of conservation specialists, scholars, publishers, book-artists, imaging specialists, engineers, and scientists who are interested in the historical practice of letterlocking. We want to make sure letters are conserved properly so that they can be studied for the historical secrets they reveal. The material features of letters can speak to us about the past, but in order to hear them we have to learn their language. Unlocking History is dedicated to bringing together all the tools we need to do so – a dictionary, instructional videos, images, and hands-on workshops in libraries, museums, universities, and schools around the world.
Letterlocking and the Dictionary of Letterlocking (DoLL)
Letterlocking refers to the technology of folding and securing an epistolary writing substrate to function as its own envelope – a vital communications technology before the invention of the mass-produced envelope in the 19th century. A full definition of letterlocking can be found in the Dictionary of Letterlocking (DoLL).
Documenting the physical details of well-preserved letters has helped us discern and define different locking formats with multiple levels of built-in security and various authentication devices. DoLL will explain the key differences between these formats – and show you how to make them. With practice, you will be able to examine flattened historical letters in libraries and archives, and make models to show you which letterlocking format the writer or secretary was using. These formats may correlate to the sensitivity of the information contained inside, or contribute to the meaning of the text they carry.
Imaging and Conservation
The study of letterlocking is important for the preservation of documents because it informs conservators about the evidential value of folds, creases, and intentional damage.
View and share images of letterlocking preservation: #PreserveTheFolds.
…
Letterlocking interests curators and historians but has advantages for modern activists as well.
Those advantages include:
- Accessible to nearly anyone
- Flummoxes the average FBI agent
- Provides visual evidence of tampering
- Slower search than digital communications
- Supports physical encryption (measurable distances)
Not to mention the use of “antiquated” technology will draw attention to the letters, whether they contain valuable or useless information. Government agents, being risk adverse, will fear some later review will prove the letters had valuable intelligence.
A trap entirely of their own making and one you should exploit whenever possible.
If that captures your interest, continue onto: A Postal Treasure Trove:
In 1926, a seventeenth-century trunk of letters was bequeathed to the Museum voor Communicatie in The Hague, then as now the centre of government, politics, and trade in The Netherlands. The trunk belonged to one of the most active postmaster and post mistress of the day, Simon and Marie de Brienne, a couple at the heart of European communication networks. The chest contains an extraordinary archive: 2600 “locked” letters sent from all over Europe to this axis of communication, none of which were ever delivered. In the seventeenth century, the recipient also paid postal and delivery charges. But if the addressee was deceased, absent, or uninterested, no fees could be collected. Postmasters usually destroyed such “dead letters”, but the Briennes preserved them, hoping that someone would retrieve the letters – and pay the postage. Hence the nickname for the trunk: “the piggy bank” (spaarpotje). The trunk freezes a moment in history, allowing us to glimpse the early modern world as it went about its daily business. The letters are uncensored, unedited, and 600 of them even remain unopened. The archive itself has remained virtually untouched by historians until it was recently rediscovered. Our international and interdisciplinary team of researchers has now begun a process of preservation, digitization, transcription, editing, and identification of letterlocking formats that will reveal its secrets for the first time – even, we hope, those of the unopened letters.
How cool is that? Letters preserved because the post office was hoping to nick the recipient for the postage!
Does that explain pay-in-advance postal systems of today. 😉
Both Letterlocking and A Postal Treasure Trove provide links to other resources on letterlocking.
A YouTube search on letterlocking returns approximately 525 videos.
On Twitter, follow @letterlocking, among others.
Any CS/Math types in the crowd who want to express letterlocking more formally? Thinking of Paper Folding Geometry and the exploration of folding algorithms more generally, such as with protein folding (except in 2 dimensions).