Microsoft Patches Word Zero-Day Spreading Dridex Malware by Tom Spring.
From the post:
Microsoft on Tuesday released a patch for a zero-day vulnerability that was discovered late last week and used to spread the Dridex banking Trojan.
Attacks were spreading via a massive spam campaign where emails contain Microsoft Word documents with malicious attachments that exploited a vulnerability in the way Microsoft handles OLE2Link objects. According to researchers, the attacks were effective at bypassing most mitigation efforts.
…
Err, well, except that Tom goes on to say:
…
However, Microsoft notes “you must have the release version of Service Pack 2 for Office 2010 installed on the computer” to apply the security update. Alternatively, security experts recommend blocking RTF documents in Microsoft Word via the File Block Settings in the Microsoft Office Trust Center. They also recommend using Microsoft Office Protected View, which they say can help prevent exploitation without user interaction.
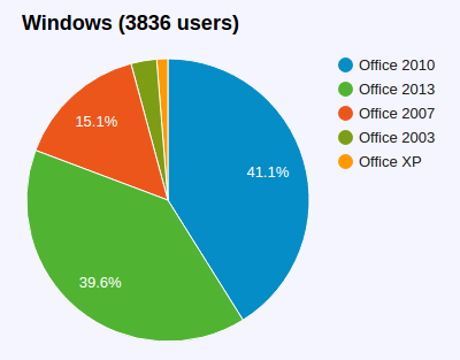
A highly unscientific survey of MS Office users at: http://www.msofficeforums.com/versionchart.php?mon=12, shows the patch leaves 56% of Office users vulnerable.
Is that the total you get?
Anyone spreading the Dridex malware need not despair about the MS patch. The majority of Office users remain unprotected.