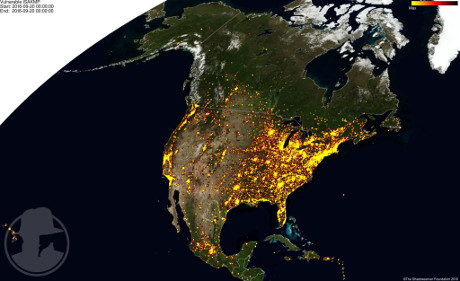
The Vulnerable ISAKMP Scanning Project, courtesy of ShadowServer reports:
This scan is looking for devices that contain a vulnerability in their IKEv1 packet processing code that could allow an unauthenticated, remote attacker to retrieve memory contents, which could lead to the disclosure of confidential information. More information on this issue can be found on Cisco’s site at: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1.
The goal of this project is to identify the vulnerable systems and report them back to the network owners for remediation.
…
Statistics on current run
859,233 distinct IPs have responded as vulnerable to our ISAKMP probe.
…
(emphasis in the original)
If visuals help:
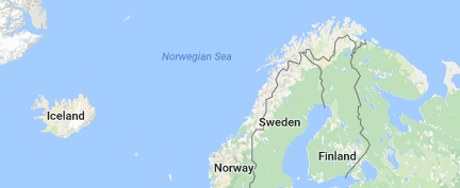
I trust your map reading skills are sufficient to conclude that ISAKMP vulnerabilities aren’t common in Iceland and northern Finland. There are more fertile areas for exploration.
You can see other land masses or all vulnerable devices.
Is anyone selling ISAKMP scan data?
That would be valuable intell.
Imagine converting it into domain names so c-suite types could cross-check reassurances from their IT departments.