NSA denies ‘Raiders of the Lost Ark’ stockpile of security vulnerabilities by Alex Hern.
From the post:
America’s National Security Agency (NSA) spends upwards of $25m in a year buying previously undisclosed security vulnerabilities – known as zero days, because that’s the length of time the target has had to fix them – but the large investment may not result in as much of a collection of hacking capabilities as is widely assumed.
Jason Healey, a senior research scholar at Columbia University and director at the Atlantic Council policy thinktank, argues that the true number of zero days stockpiled by the NSA is likely in the “dozens”, and that the agency only adds to that amount by a very small amount each year. “Right now it looks like single digits,” he says, adding that he has “high confidence in this assessment.”
…
One key piece of evidence comes from the NSA itself, which in 2015 claimed that 91% of vulnerabilities it procured were eventually disclosed to the vendors whose products were at risk. Of the other 9%, at least some of those weren’t disclosed because they were fixed before they could be, the agency adds.
Similarly, the White House has revealed that in one year since the current disclosure policy was implemented, it reviewed about 100 software vulnerabilities discovered by the NSA to determine if they should be disclose, and “kept only about two”. Healey adds that in the autumn of 2014, he was personally told that every single vulnerability which had come up for review had been disclosed.
…
No amount of factual reporting is likely to dispel the myth of an NSA horde of zero days.
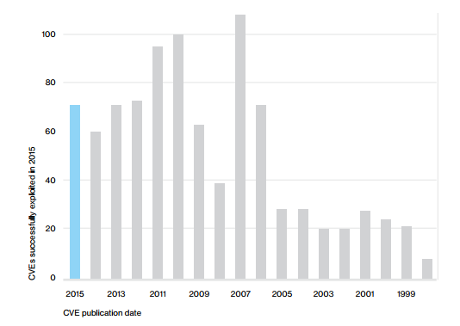
However, the Verizon 2016 Data Breach Investigations Report makes it clear that zero days aren’t the main source of hacking danger:
That’s not an error! Vulnerabilities prior to 1999 are still in use.
You can spend your days discussing rumors of the latest zero day or you can insist that IT follow a verified application of patches process.
How effective is patching known vulnerabilities?
The top 10 internal vulnerabilities accounted for over 78 percent of all internal vulnerabilities during 2015. All 10 internal vulnerabilities are directly related to outdated patch levels on the target systems. (2016 NTT Group, Global Threat Intelligence Report, page 5. Emphasis in original.)
Routine patching can reduce your internal vulnerabilities by 78% (on average).
That’s a clear, actionable, measurable requirement.
Call up your IT department, ask for a list of all the software in your enterprise and a list of patches that have been applied to each instance and those waiting to be applied (as per the vendor).
Remember, a data breach maybe ITs “fault,” but it may be your job that is at risk.
PS: One of earliest uses of topic maps was to track software on a university network.