Cisco 2015 Midyear Security Report
A must read for this graphic is nothing else:
Select (“click”) for a larger version.
The top three?
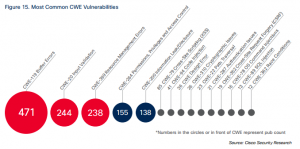
- Buffer Errors – 471
- Input Validation – 244
- Resource Management Errors – 238
If we assume that #4, Permissions, Privileges and Access Control – 155 and Information Leak/Disclosure – 138, are not within a vendor’s control, the remaining 295 are. Added to the top three vulnerabilities, vendor preventable vulnerabilities total 1245 out of 1541 or 81% of the vulnerabilities in the graphic.
Cisco has an answer for why this pattern repeats year after year:
The problem lies in insufficient attention being paid to the secure development lifecycle. Security safeguards and vulnerability tests should be built in as a product is being developed. Instead, vendors wait until the product reaches the market and then address its vulnerabilities.
You can’t say that Cisco is anti-vendor, being a software vendor itself.
Under current law, it is cheaper for software vendors to fix only the vulnerabilities that are discovered (for free) by others.
Yes, the key phrase is “under current law.”
Strict liability and minimum (say $5K) damages for
- Buffer Errors
- Input Validation
- Resource Management Errors
would be a large step towards eliminating 62% of the vulnerabilities each year.
Vendors would not have to hunt for every possible vulnerability, just those that fall into those three categories. (To blunt the argument that hunting vulnerabilities is sooo difficult. Perhaps but I propose to eliminate only three of them.)
Strict liability would eliminate all the tiresome EULA issues for all plaintiffs.
Mandatory minimum damages would make finding lawyers to bring the suits easy.
Setting specific vulnerability criteria limits the cry that “perfect” software isn’t possible. True, but techniques to avoid buffer overflows existed in the 1960’s.
Users aren’t asking for perfection but that they and their files have a higher status than digital litter.