Russian researchers expose breakthrough U.S. spying program by Joseph Menn.
From the post:
The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world’s computers, according to cyber researchers and former operatives.
That long-sought and closely guarded ability was part of a cluster of spying programs discovered by Kaspersky Lab, the Moscow-based security software maker that has exposed a series of Western cyberespionage operations.
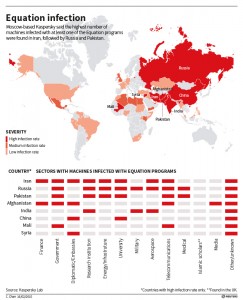
Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists, Kaspersky said. (reut.rs/1L5knm0)
Don’t have a sense for all thirty countries? Reuters has a visual to help with that:
The Reuters report is great but if you want more technical details, see: Equation Group: The Crown Creator of Cyber-EspionageThe original Kaspersky report, and Equation: The Death Star of Malware Galaxy by GReAT (Kaspersky Labs’ Global Research & Analysis Team), which is an in depth review of the exploit.
There is a comment to the GReAT blog post that reads:
Ok, reading through NSA files that Der Spiegel released i found this:
http://www.spiegel.de/media/media-35661.pdf
This is a file that shows the job postings for NSA interns, you can find a NSA wiki link in the last page. And this is very interesting:
(TS//SI//REL) Create a covert storage product that is enabled from a hard drive firmware modification. The ideia would be to modify the firmware of a particular hard drive so that it normally only recognizes half of its available space. It would report this size back to the operating system and not provide any way to access the additional space.
This is a 2006 document, it took 8 years to finish this product, which is what kaspersky found.
So maybe you guys would easily find the malware if you revert the firmware to a state prior of this date.
Has anyone been collecting hard drive firmware? Another example of where “secret” code exposes users to dangers difficult to guard against.
Public open source code (whether “free” or not) should be a legal requirement for the distribution of software and/or devices with firmware. Just for security reasons alone.
BTW, anyone still in favor of “trusting” the intelligence community if they say your privacy is being respected?
I found the Reuters story because of a tweet by Violet Blue. I then tracked down the source documents for your convenience (I haven’t seen them in other accounts).