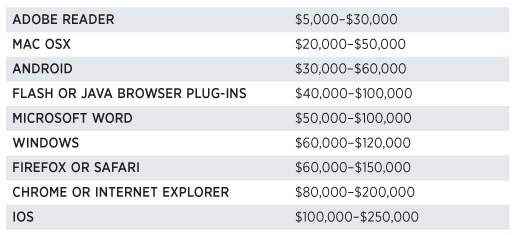
A price guide for zero day exploits was reported in Shopping For Zero-Days: A Price List For Hackers’ Secret Software Exploits by Andy Greenberg:
A rough guide as reliable sales information is hard to obtain.
But accurate enough to know that Tavis Ormandy (see: Google Researcher Reveals Zero-Day Windows Bug by Mathew J. Schwartz) dropped the ball when he:
published full details for a zero-day Windows vulnerability, including proof-of-concept (PoC) exploit code.
A weakness present in Windows 7 and 8, possibly going back 20 years in Windows.
With the number of legacy Windows systems, particularly in government offices, that should have pushed the price up substantially.
Buyers of software exploits want for secrecy to preserve an exploit’s value. Leaving brokers as the best marketing strategy for software exploits.
But what if the weaponized information, even if known, was unlikely to change?
For example, mapping response times by fire/police to metropolitan maps? Or locations of accidents that cause the longest traffic delays?
The data is available but not always assembled for easy reference. Subject to legitimate as well as illegitimate uses.
Where would you market it them? How would you price them?
Suggestions?
Update
I encountered the story about the zero-day exploit for Windows almost two weeks later in: Google researcher discloses zero-day exploit for Windows. Slight differences. H associates were able to reproduce the bug. Opening a file is sufficient to run programs with system privileges, even with a guest account.