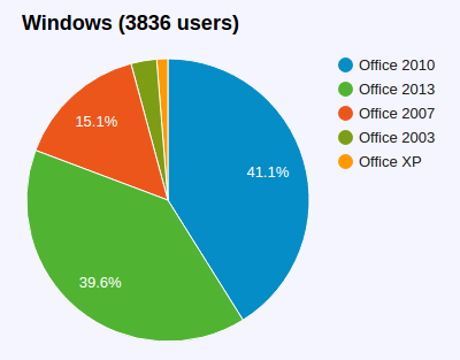
If you haven’t seen images from the I-85 fire in Atlanta, which caused a 100 foot section of a bridge to collapse, consider:

resulted in:

The fire being powered by HPDE coils:

HPDE coils burn at 341 degrees, according to its manufacturer.
One more fact you need:
Q: What is the temperature of a Bic lighter flame?
A: The temperature of a Bic lighter can reach nearly 1,977 degrees Celsius or 3,590.6 degrees Fahrenheit. The temperature of a lighter’s flame depends on what type of fuel the lighter uses. Bic lighters use butane and are called butane lighters.

From: https://www.reference.com/science/temperature-bic-lighter-flame-1ca2e364e38d1085 (emphasis added)
It has been alleged a mentally ill crackhead (there’s some other kind?) set furniture on fire, which spread to other materials and then the HPDE coils.
I mention this after having read I write thrillers. My research showed me how easily terrorists can strike us by Matthew Quirk.
Quirk writes in part:
A gray SUV idled across the street from the chemical plant. Gas storage tanks, four stories tall, towered over the low-slung neighborhood. It was a hot, dry Sunday in southeast Los Angeles.
The plant’s front gate was open. The driver tapped the throttle, then cut into the facility, past the “no trespassing” notices and the signs demanding that all trucks stop and check in with a guard. He pointed the car straight at three trailers loaded with compressed hydrogen. Behind them, on the other side of a rusting chain-link fence, rail tankers sat outside a facility that uses chlorine to manufacture bleach. One tanker car of chlorine, if ruptured (by, say, a nearby hydrogen explosion), could reach 4.9 million people in the Los Angeles Basin and kill 10,000 under worst-case conditions.
The driver veered away from the gas tanks, then stopped the car and waited. No one came to check on him as he took a few photos on his phone. After five minutes, he pulled away.
That was me. I write thrillers for a living. For my latest novel, “Dead Man Switch,” I spent a lot of time researching the materials lying around the United States that terrorists could use to kill tens of thousands of people. I like to think my books are pretty tense, but they have nothing on reality: More than 15 years after 9/11, we have failed to take basic steps to address glaring threats that have already cost American lives.
With its ongoing attempts to enact a ban on many Muslim travelers and “extreme vetting” for visitors to the United States, the Trump administration has treated terrorism as a political cudgel rather than the grave and present threat it truly represents. In the years after 9/11, there was extraordinary bipartisan momentum to identify threats and safeguard against them, but the work is unfinished. With terrorism back atop the agenda, we should spend our time and money addressing the obvious risks, not the hypothetical or concocted ones.
… (emphasis added)
I disagree with Quirk and Washington Post on their assessment of the risk of terrorist attacks but have to second addressing actual risks and not imaginary ones.
Security speakers who wax eloquently about smallpox infected travelers and weaponized anthrax, fail to recognize a good Mission Impossible plot when they see one. Things like HPDE coils, Interstate bridges and Bic lighters escape their notice.
Terrorism doesn’t require elaborate cell infrastructures, much and unfairly maligned encrypted cellphone apps, or any of the highly convoluted schemes in popular fiction (read Homeland Security reports).
No, if I were concerned about terrorism, it would be over garden variety terrorism. The sort that uses no tool or implement not readily available to the average home owner.
Perhaps using those tools/implements in unexpected ways, in combination with open data to create, what did the American general say about Tet (1968)? Oh, yes, “to create maximum consternation.”