For an emergency view of the Apple/NSO Trident 0days issues, you can read Apple tackles iPhone one-tap spyware flaws (BBC), Apple issues security update to prevent iPhone spyware (USATODAY), or IPhone Users Urged to Update Software After Security Flaws Are Found (NYT).
On the other hand, Robert Graham, @ErrataRob, says its just another day of 0days:
…
Press: it’s news to you, it’s not news to us
I’m seeing breathless news articles appear. I dread the next time that I talk to my mom that she’s going to ask about it (including “were you involved”). I suppose it is new to those outside the cybersec community, but for those of us insiders, it’s not particularly newsworthy. It’s just more government malware going after activists. It’s just one more set of 0days.
I point this out in case press wants to contact for some awesome sounding quote about how exciting/important this is. I’ll have the opposite quote.
Don’t panic: all patches fix 0days
We should pay attention to context: all patches (for iPhone, Windows, etc.) fix 0days that hackers can use to break into devices. Normally these 0days are discovered by the company itself or by outside researchers intending to fix (and not exploit) the problem. What’s different here is that where most 0days are just a theoretical danger, these 0days are an actual danger — currently being exploited by the NSO Group’s products. Thus, there’s maybe a bit more urgency in this patch compared to other patches.
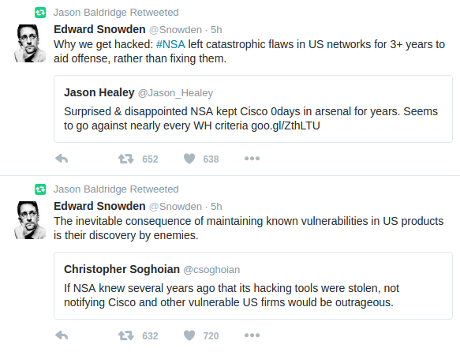
Don’t panic: NSA/Chinese/Russians using secret 0days anyway
It’s almost certain the NSA, the Chinese, and the Russian have similar 0days. That means applying this patch makes you safe from the NSO Group (for a while, until they find new 0days), but it’s unlikely this patch makes you safe from the others.
… (Notes on the Apple/NSO Trident 0days)
Taking all communication systems as insecure, digital ones in particular, ErrataRob’s position has merit.
However, the consequences of a lapse of security for someone like Ahmed Mansoor, are far from trivial.
Consider this passage from the executive summary in The Million Dollar Dissident: NSO Group’s iPhone Zero-Days used against a UAE Human Rights Defender:
Ahmed Mansoor is an internationally recognized human rights defender, based in the United Arab Emirates (UAE), and recipient of the Martin Ennals Award (sometimes referred to as a “Nobel Prize for human rights”). On August 10 and 11, 2016, Mansoor received SMS text messages on his iPhone promising “new secrets” about detainees tortured in UAE jails if he clicked on an included link. Instead of clicking, Mansoor sent the messages to Citizen Lab researchers. We recognized the links as belonging to an exploit infrastructure connected to NSO Group, an Israel-based “cyber war” company that sells Pegasus, a government-exclusive “lawful intercept” spyware product. NSO Group is reportedly owned by an American venture capital firm, Francisco Partners Management.
The ensuing investigation, a collaboration between researchers from Citizen Lab and from Lookout Security, determined that the links led to a chain of zero-day exploits (“zero-days”) that would have remotely jailbroken Mansoor’s stock iPhone 6 and installed sophisticated spyware. We are calling this exploit chain Trident. Once infected, Mansoor’s phone would have become a digital spy in his pocket, capable of employing his iPhone’s camera and microphone to snoop on activity in the vicinity of the device, recording his WhatsApp and Viber calls, logging messages sent in mobile chat apps, and tracking his movements.
We are not aware of any previous instance of an iPhone remote jailbreak used in the wild as part of a targeted attack campaign, making this a rare find.
…
ErrataBob’s point that 0days are everywhere and all governments have them, doesn’t diminish the importance of the patch for iPhone users or provide a sense of direction for what’s next?
Here’s a 0day policy question:
Does disclosure of 0days to vendors disarm citizens while allowing governments to retain more esoteric 0days?
Governments are not going to dis-arm themselves of 0days so I see no reason for “responsible disclosure” to continue to disarm the average citizen.
Technical analysis of the NSO Trident 0days: The Million Dollar Dissident: NSO Group’s iPhone Zero-Days used against a UAE Human Rights Defender, and Technical Analysis of Pegasus Spyware.
Both of those reports will give you insight into this attack and hopefully spur ideas for analysis and attack.
BTW, the Apple software update.