Sophisticated, chilling, alarming, nefarious, vicious, are all terms used to describe the recent HBO hack.
For your reading pleasure, try HBO Hack: Insiders Fear Leaked Emails as FBI Joins Investigation by Tatiana Siegel, or HBO Security Contractor: Hackers Stole ‘Thousands of Internal Documents’ (EXCLUSIVE) by Janko Roettgers
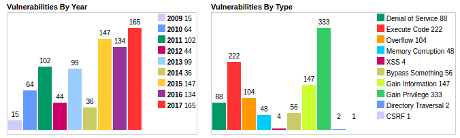
There’s a shortage of facts available concerning this hack of HBO (Home Box Office) but 1.5 terabytes is being thrown around as a scary number for the data loss.
While everyone else oohs and aahs over 1.5 terabytes of data, you can smile knowing that a new Dell XPS 27 sells pre-configured with a 2 terabyte drive for $1899.99, shipping, taxes, blah, blah extra. That’s a mid to low range desktop.
Hackers may have gotten 1.5 terabytes of data but that’s no indication of its worth. How do you count emails with dozens of people on the cc: line? Or multiple versions of the same video?
I don’t have time to watch the majority of HBO content on my legitimate subscription so I’m not interested in the stolen content, assuming it includes anything worth watching.
Of greater interest is forensic analysis of how the hack was performed, because post-Sony, one expects HBO avoided the obvious faults that led to the Sony hack. If they did, perhaps there is something to be learned here.
Unlike the Podesta “hack,” which consisted of losing his email password in a phishing attack. That’s not really a hack, that’s just dumb
Watch your favorite sites for alleged HBO content.
Alleged HBO content with viruses, malware and ransomeware! Oh, my!