Journalists are likely to get USB sticks from unknown and/or untrustworthy sources. CIRCLean copies potentially dangerous files on an untrustworthy USB stick, converts those files to a safe format and saves them to your trusted USB stick. (Think of it as not sticking a potentially infected USB into your computer.)
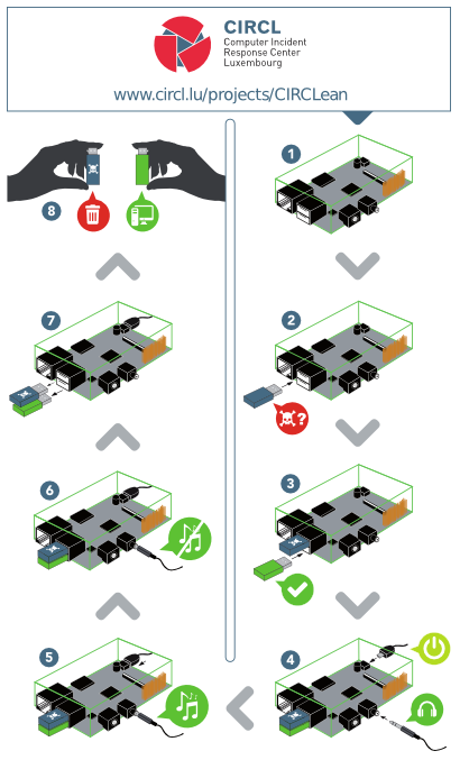
Visual instructions on using CIRCLean:
Written instructions based on those for CIRCLean, without illustrations:
- Unplug the device.
- Plug the untrusted USB stick into the top usb slot.
- Plug your own, trusted USB stick into the bottom usb slot.
- Connect the power to the device.
- If your device has a diode, wait until the blinking stops.
- Unplug the device and remove the USB keys
Note: Make sure your USB stick is bigger than the untrusted one. The extracted documents are sometimes bigger than the original ones.
Otherwise, plug a headset and listen to the music that is played during the conversion. When the music stops, the conversion is finished.
Label all untrusted USB sticks. “Untrusted” means it has an origin other than you. Unicode U+2620 ‘skull and crossbones” works, ☠. Or a bit larger:

(Image from http://graphemica.com/)
It’s really that easy!
On The Flip Side
Modifying the CIRCLean source to maintain its present capabilities but adding your malware to the “trusted” USB stick offers a number of exciting possibilities.
Security is all the rage in the banking industry, making a Raspberry Pi (with diode), an attractive case, and your USB malware great banking convention swag.
Listing of banking conferences are maintained by the American Bankers Association, the European Banking Association, and Asian Banking & Finance, to name just a few.
A low-cost alternative to a USB cleaning/malware installing Raspberry Pi would to use infected USB sticks as sway. “Front Office Staff: After Hours” or some similar title. If that sounds sexist, it is, but traps use bait based on their target’s proclivities, not yours.
PS: Ethics/legality:
The ethics of spreading malware to infrastructures based on a “white, cisheteropatriarchal*” point of view, I leave for others to discuss.
The legality of spreading malware depends on who’s doing the spreading and who’s being harmed. Check with legal counsel.
* A phrase I stole from: Women’s Suffrage Leaders Left Out Black Women. A great read.