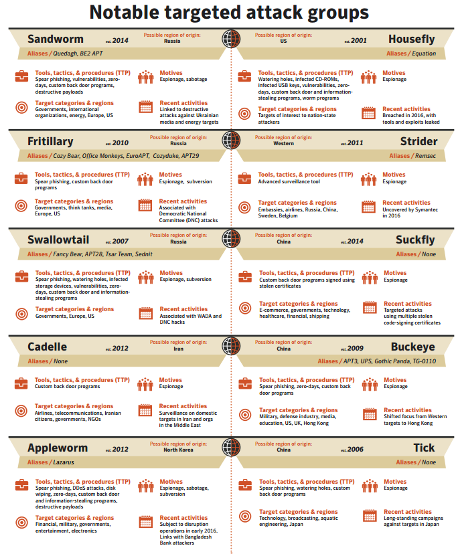
Symantec continues the Sears Wish Book tradition:
for hackers with the 2017 Internet Security Threat Report (Symantec, ISTR 22).
Like the original, the Hacker Wish Book 2017 has:
Flashy graphics:
(Did you make the top ten?)
Exciting textual tidbits:
…
Our data found that 76 percent of websites scanned contained vulnerabilities—the same percentage as 2014 and just two percent less than the 2015 figure. at page 33)
…
Holiday tips (best practices):
- Targeted attacks: Espionage, subversion, & sabotage (page 22)
- Email: Malware, spam, & phishing (page 31)
- Web attacks, toolkits, & exploiting vulnerabilities online (page 36)
- Cyber crime & the underground economy (page 54)
- Ransomware: Extorting businesses & consumers (page 62)
- New frontiers: Internet of Things, mobile, & cloud threats (page 67)
- Mobile (page 72)
- Cloud (page 74)
Who Was Left Out?
Before you print a full-color copy of 2017 Internet Security Threat Report (Symantec, ISTR 22) for your “reading” room, ask who was left out?
Hackers are covered by the list of schemes, devices and strategies. Managers are interested in comparative statistics, “see, almost everybody else gets hacked too.” Hmmmm, but a class of people are missing.
Here’s a hint: Use the search function to look for salary (0 hits), hiring (0 hits), training (0 hits), compensation (0 hits).
The cyberdefense community gets no joy from the Hacker Wish Book 2017.
Not one mention of the need to pay competitive compensation for cyberdefense employees (not part-time contractors) with benefits and working conditions suitable for that community.
We have all seen legislatures flail about on cybercrime (CFAA). Not to mention management’s foolish belief that urging present staff “to do better,” is a solution to cyber-insecurity (the best practices mentioned above).
If you credit the Symantec report at all, how would you grade both of those strategies?
If your answer is anything other than “F,” contact me as I have the deed to bridges in New York City. (Apologies to other readers, it’s hard to resist clipping business types with more money than judgment.)
Anyone interested in improved cybersecurity needs to invest in cybersecurity. Including full-time staff and resources.
When I say “full-time” staff, I mean just that. Not sysadmin, DBA, webmaster, and cybersecurity all rolled into one position. Any one of those, with further sub-specialization as necessary, is a full-time job. (Just because you don’t understand a task doesn’t make it easy.)
Of course you can have your data breach figure in the Hacker Wish Book 2018. Or be the first in your industry to get tagged with punitive damages for a data breach. That’s going to happen. The question is: Will it be you?
Your call.