Apple CORED: Boffins reveal password-killer 0-days for iOS and OS X by Darren Pauli.
From the post:
Six university researchers have revealed deadly zero-day flaws in Apple’s iOS and OS X, claiming it is possible to crack Apple’s password-storing keychain, break app sandboxes, and bypass its App Store security checks.
Attackers can exploit these bugs to steal passwords from installed apps, including the native email client, without being detected.
The team was able to upload malware to Apple’s app stores, and passed the vetting processes without triggering any alarms. That malware, when installed on a victim’s Mac, raided the keychain to steal passwords for services including iCloud and the Mail app, and all those stored within Google Chrome.
Lead researcher Luyi Xing told El Reg he and his team complied with Apple’s request to withhold publication of the research for six months, but had not heard back as of the time of writing.
They say the holes are still present in Apple’s software, meaning their work will likely be consumed by miscreants looking to weaponize the work.
Apple was not available for immediate comment.
The Indiana University boffins Xing; Xiaolong Bai; XiaoFeng Wang; and Kai Chen joined Tongxin Li, of Peking University, and Xiaojing Liao, of Georgia Institute of Technology, to develop the research, which is detailed in a paper titled Unauthorized Cross-App Resource Access on Mac OS X and iOS.
See Darren’s post for more non-technical details and the paper for the full monty.
Is your first impulse on reading about Apple CORED to run out and buy stock in security software companies that don’t address the underlying vulnerability? No? Perhaps because security software doesn’t address the underlying problem? Or perhaps because security software could have its own vulnerability to add to the maze of known and unknown vulnerabilities of your own IT stack?
You should feel smart today because a lot of investors aren’t as bright as you. The Billion-Dollar Bet That Better Software Can Back Off Hackers by Joseph Ciolli, is more appropriately titled: The Billion-Dollar Theft That Better Software Can Back Off Hackers.
From Joseph’s post:
About the only thing rising as fast as online mischief is the stock of firms trying to thwart it.
Companies from FireEye Inc. to Palo Alto Networks Inc. have taken off in 2015, extending the gain in a four-year-old index tracking network security firms past 200 percent. An exchange-traded fund tied to the shares just surpassed $1 billion in market value, having doubled in size since the start of April.
Online intrusions such as last week’s breach of confidential government employee records have fanned cyber paranoia, boosting spending on network security and making darlings out of companies with a hand in safeguarding digital data. The theme is starting to feed on itself among investors afraid of being left out.
“This is an industry where the higher the price goes, the more attractive it becomes to people,” said John Manley, who helps oversee about $233 billion as chief equity strategist for Wells Fargo Funds Management in New York. “It’s been a herd mentality in these stocks as these companies offer a level of security that wasn’t offered before.”
A 24 percent gain in 2015 and a frenzy of investor inflows swelled the market value of the PureFunds ISE Cyber Security ETF past the $1 billion threshold on Tuesday. That’s up from $107 million at the start of the year and $494 million at the end of the first quarter.
…
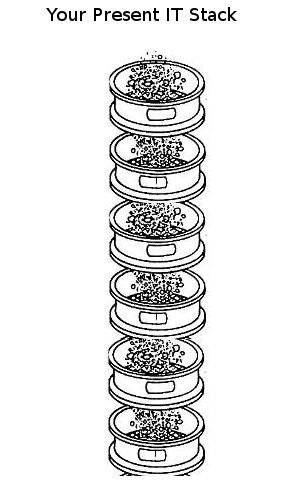
I have been practicing with Gimp and here is how I would visualize the present security dilemma.
As you can see, your present IT stack is holes all the way down. That is the crux of the current security dilemma. Not that the network has vulnerabilities or your OS has vulnerabilities or that applications have vulnerabilities or that your hardware has vulnerabilities. Holes all the way down.
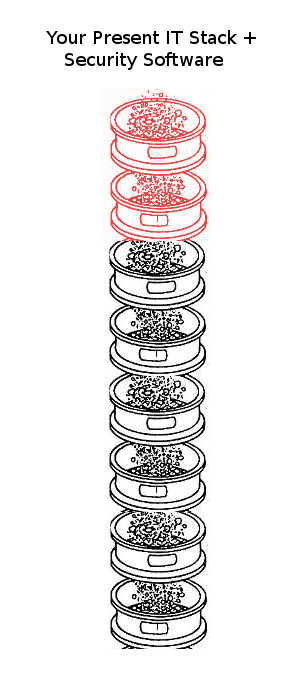
The $billion software solution makes your IT stack look like this:
I colored the security software contribution to your stack in red to symbolize its impact on your bottom line.
The answer to cybersecurity is NOT better but leaky security software on top of a leaky IT stack.
The answer to cybersecurity IS better software in the IT stack. Security as an integral part of software design.
With the rising tide of data breaches, it won’t be that long before some judge is quoting these lines in a judgement against a software vendor:
To establish the manufacturer’s liability it was sufficient that plaintiff proved he was injured while using the [product] in a way it was intended to be used as a result of a defect in the design and manufacture of which the plaintiff was not aware that made the [product] unsafe for its intended use. (Greenman v. Yuba Power Products, Justice Traynor)
I found that quote in a delightful summary on product liability law, An Introduction to Product Liability Law by Dennis W. Stearns. The summary only runs thirteen pages and 1,000+ page tomes exist on the subject. Use the summary as a starting point, not an end point.