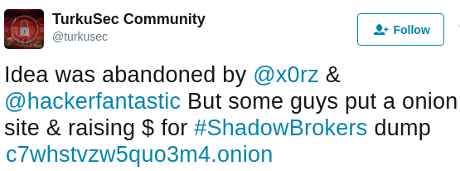
WikiLeaks offers $10,000 to get Intercept reporter fired by Joe Uchill.
From the post:
WikiLeaks offered a $10,000 bounty Monday aimed at getting a reporter for The Intercept fired, following the arrest of a government contractor who allegedly leaked an NSA report to the site.
The Justice Department announced earlier Monday that it had arrested Reality Leigh Winner, a 25-year-old government contractor, for leaking classified documents to a news organization. It has been widely reported that Winner allegedly leaked documents from the NSA to The Intercept about Russian attempts to hack U.S. elections officials.
Investigators were able to find Winner in part, according to a government court filings, because of clues gained when an Intercept reporter showed the leaked report to the government.
…
The Intercept article lists four reporters:
From the affidavit for Reality Leigh Winner’s arrest:
…
12. On June I, 2017, the FBI was notified by the U.S. Government Agency that the U.S. Government Agency had been contacted by the News Outlet on May 30, 2017, regarding an upcoming story. The News Outlet informed the U.S. Government Agency that it was in possession of what it believed to be a classified document authored by the U.S. Government Agency. The News Outlet provided the U.S. Government Agency with a copy of this document. Subsequent analysis by the U.S. Government Agency confirmed that the document in the News Outlet’s possession is the intelligence reporting. The intelligence reporting is classified at the Top Secret level, indicating that its unauthorized disclosure could reasonably result in exceptionally grave damage to the national security, and is marked as such. The U.S. Government Agency has since confirmed that the reporting contains information that was classified at that level at the time that the reporting was published on or about May 5, 2017, and that such information currently remains classified at that level.13. The U.S. Government Agency examined the document shared by the News Outlet and determined the pages of the intelligence reporting appeared to be folded and/or creased, suggesting they had been printed and hand-carried out of a secured space.
…
Why on earth?:
The News Outlet provided the U.S. Government Agency with a copy of this document.
How sloppy is that?
Do you trust the “U.S. Government Agency” given a copy of the document to out the reporter in question?
Or does this give them a free shot at a good reporter and blackmail evidence on the real culprit?
Suggestions?