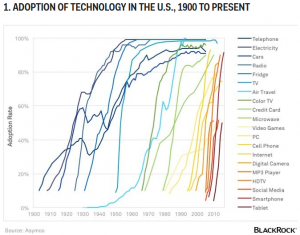
Government hints it may demand iOS source code, signing key by Gregg Keizer.
Gregg points out that the latest brief by the DOJ in the San Bernardino case, at footnote 9, page 22, the government says:
9 For the reasons discussed above, the FBI cannot itself modify the software on Farook’s iPhone without access to the source code and Apple’s private electronic signature. The government did not seek to compel Apple to turn those over because it believed such a request would be less palatable to Apple. If Apple would prefer that course, however, that may provide an alternative that requires less labor by Apple programmers. See In re Under Seal, 749 F.3d 276, 281-83 (4th Cir. 2014) (affirming contempt sanctions imposed for failure to comply with order requiring the company to assist law enforcement with effecting a pen register on encrypted e-mail content which included producing private SSL encryption key).
The DOJ hints that it will enlist the courts to assist it in the theft of Apple’s property and as Gregg further points out, may still want to force Apple to assist it:
Even if the Court ordered Apple to provide the government with Apple’s cryptographic keys and source code, Apple itself has implied that the government could not disable the requisite features because it “would have insufficient knowledge of Apple’s software and design protocols to be effective.” (Neuenschwander Decl. ¶ 23.) (at page 28 of the latest government brief)
Powerful briefs have been filed in support of Apple but its time to take the factual gloves off.
The expansive claims of the government are based solely on the entirely fictional notion that it is in hot pursuit of a terrorist threat.
If there were any terrorist threat to speak of, one would expect the TSA to have found a terrorist, at least one, this many years after 9/11. Some fifteen years this next September 11th. But it hasn’t.
Yes, fourteen people died during the San Bernardino attack, which the government has yet to show was anything more than a work place related dispute that erupted at a holiday party.
No government, not even the United States government, is entitled to declare facts not in evidence and expect others, especially fact finders such as courts, to meekly accept them as true.
The DOJ keeps posturing about the government’s interest. Apple and others should put that interest to a factual test.
Government agents are engaging in budget justifying behavior is a far less compelling reason to violate Apple’s constitutional rights than an actual terrorist threat.
But the so-called terrorist threat doesn’t exist. One suspects that is why the DOJ has omitted any factual basis for its claims. It could easily whistle up all the FBI arrests for terrorism, but that would expose the recruitment of the mentally ill people who are then supplied by the FBI to make those arrests.
I’m guessing that would diminish the government’s case in the eyes of the fact finder.
In some cases the government has a compelling interest, but fictional compelling interests don’t count.
The DOJ should be challenged at every step of the process, building a factual record that consists of everyone who had any part in the San Bernardino investigation, conversations with Apple, staff of the various DOJ offices, along with office notes, records, and phone logs.
If the interest of the government is so compelling, then it should not be reluctant to make a factual demonstration for the record.
Will the DOJ build a factual record? Will Apple demand it?